Releases in 2020
September 2020 - v3.03.0
------------------------
- **User Experience Improvements**
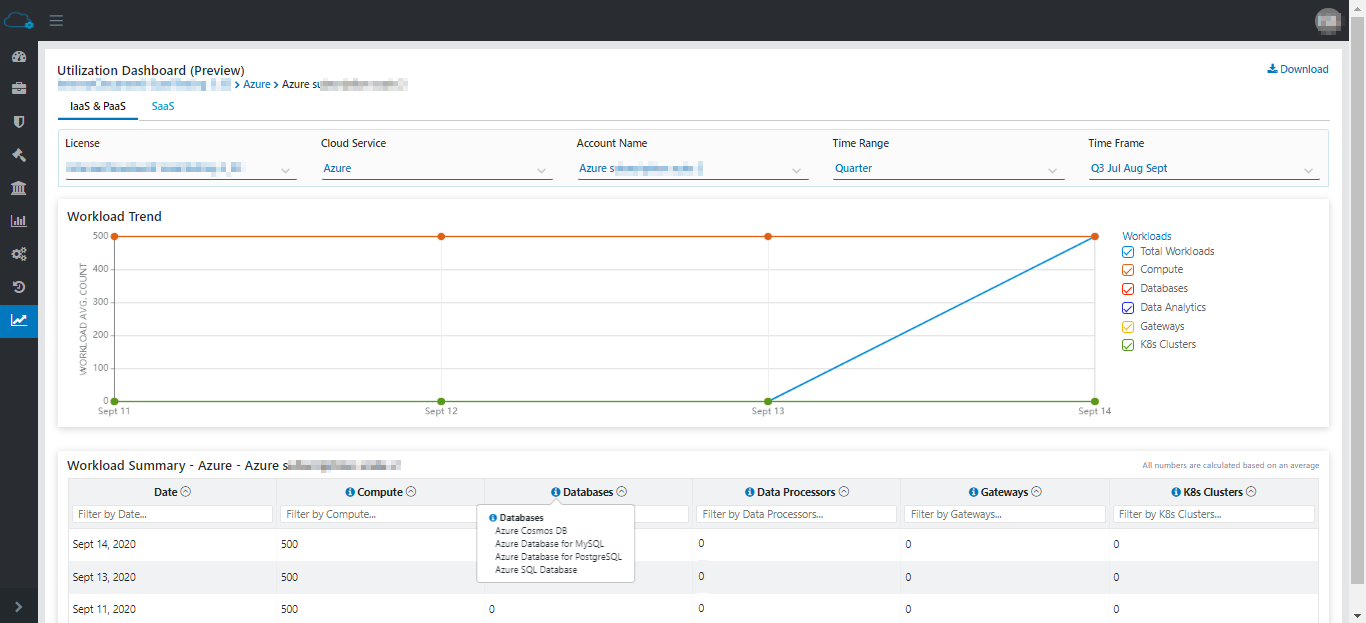
- **Updated** the *Utilization dashboard* this release provides billing
visibility to the consumed workload capacity. Customers/Partners can now use
the workload consumption data to calculate the monthly/yearly invoices
across all accounts in a license. [Refer documentation](../../administratorGuide/utilizationDashboard/#utilization-visibility-for-the-cloud-account-utilization-based-on-workloads)
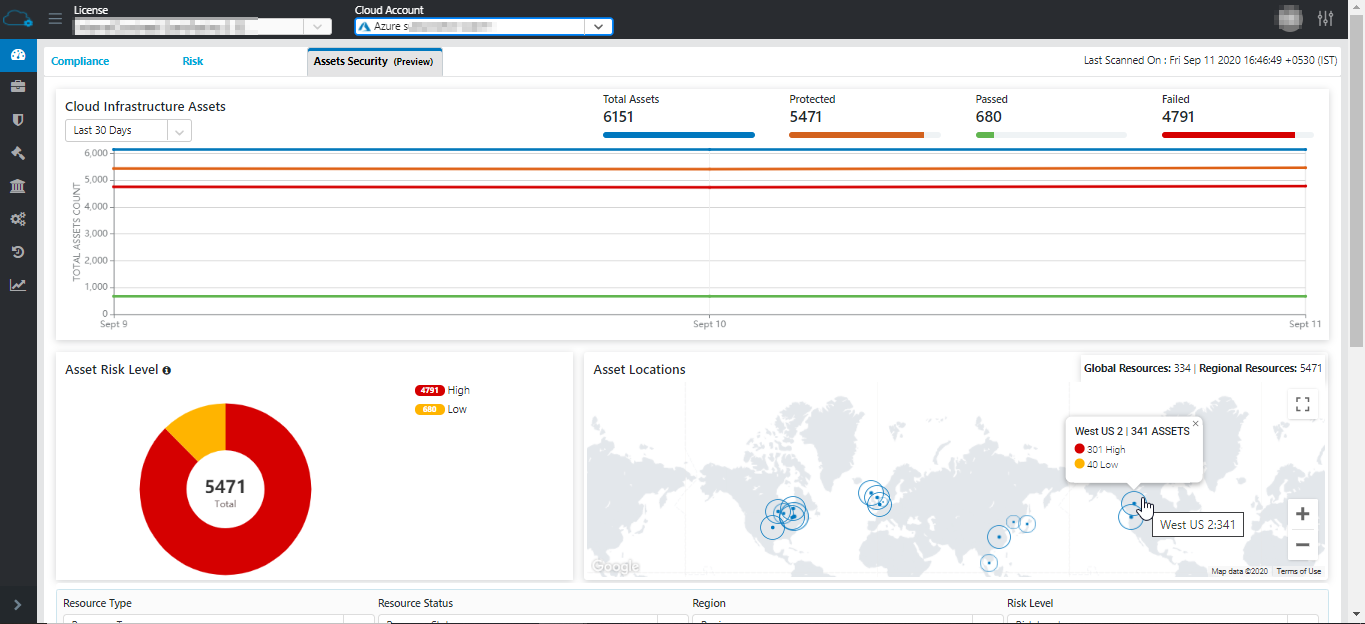
- **Updated** the *Asset Security Dashboard* to have asset visibility aggregated
at license level for asset compliance status and risk. filtering options added for
Asset type, region, compliance status, risk level, tags. [Refer documentation](../../userGuide/dashboards/#assets-security-preview)
- **GCP integration (preview)** Onboard of GCP Projects and Organizations to Zscaler CSPM now supported. Customer will be able to get security & compliance posture for various Identity & Access Management (IaM), Compute instances, Storage Buckets, Networks, etc. [Refer documentation](../../onboardingGuide/gcpOnboardingOverview/)
- **Platform & Stability Improvements**
- **Updated** AWS Data collection and processing mechanisms to use AWS config
to support massive scale requirements for the following AWS services.
- **Fixed** following bugs
- Incorrect reference link on AWS onboarding health status for 'Z CSPM
Agent on Kubernetes configuration for last execution'
- After executing IAM runbook, 4 policies are not visible on Cloud Security Best Practices and CIS
- Policy is not working properly "Ensure access keys are rotated every 90
days or less"
- CMMC logo missing on features and quotas under compliance frameworks for
"CyberSecurity Maturity model certification" Benchmark.
- K8s Clusters' is misspelled on Utilization dashboard
- Remediation applicable flag is false for 'Ensure that Termination
Protection feature is enabled for AWS CloudFormation stacks' policy
- Associate K8s cluster screen is visible for M365 accounts
- AWS::EC2::Windows2016::BaselinePolicy showing incorrect resource in
Assets Security Page
- Getting error on onboarding health status page intermittently for any
cloud account (migrated license) specifically for Azure AWS.
- Policy is having different control number on CMMC benchmark
- Data is not visible on Summary table for previous months for all
connector types when All Accounts is selected
- Spelling error 'Regenearate' instead of 'Regenerate' on Onboarding
health status page reference link
- Incorrect resources for Virtual network are displayed on Policy Details
page in CSBP
- **Updates to Security Policies & Benchmarks**
- **Updated Audit and Remediation steps for 42 Azure policies from below categories**
- Azure - Business continuity and DR
- Azure - Compute (PaaS and Serverless)
- Azure - Data in Transit
- Azure - Logging and Auditing
- Azure - Storage and Databases
- **Updated Audit and Remediation steps for 213 AWS from below categories**
- AWS - Identity and Access Management
- AWS - Data In Transit Encryption
- AWS - Compute
- AWS - Networking
- AWS - Business Continuity
- AWS - Monitoring
- AWS - Audit and Logging
- AWS - Storage and Databases
- AWS - Data Protection
- AWS - Governance
August 2020 - v3.02.0
----------------------
- **User Experience Improvements**
- **Updated** the *Utilization dashboard* for additional filter and UI updates.
- *Note* - *Please note that Resource trend graph will show data collected from latest version (3.02) scans*
- **Updated** the *Onboarding Health Status* page to include Kubernetes health status separated for cluster hosting type.
- **Platform & Stability Improvements**
- **Updated** platform by deploying multiple instances (horizontal scaling) to support massive scale requirements for the across Cloud Service Providers (CSP) like Azure, AWS.
- **Fixed** following bugs
1. On-boarding procedure link for Azure account getting redirected to
Amazon EKS
2. Health status check for AWS remediation should be re sequenced and
updated link
3. Blank Compliance Dashboard page is displayed after clicking on Cancel
button of Add Cloud Account page.
4. Mismatch in count of Security groups on AWS asset security dashboard
5. Benchmark logo is not visible in PDF Report
6. Audit logs are not generating when user updates the ServiceNow/Zendesk
configuration
7. Docs: Incorrect URL resolution for docs links on Z-help page
8. Incorrect resource count on Asset Security dashboard for Azure scaled
account
9. Fixed issues in Private Benchmark Collaboration
10. Getting error "Invalid or expired token" on subscribing Marketplace Paid
offer and navigating to Cloudneeti
11. Aggregated billing dashboard shows incorrect values for resource and
user tiles
- **Updates to Security Policies & Benchmarks**
- **Added** the following benchmark for AWS, Azure, and Office 365 cloud accounts.
- Cybersecurity Maturity Model Certification (CMMC)
July 2020 - v3.01.0
-------------------
- **User Experience Improvements**
- **Updated** Product branding to Zscaler theme across all pages, controls,
Email notifications, etc.
- **Updated** the ‘Onboarding Health Status’ page to include new Account level
checks of AWS Role and external id, AWS remediation and Kubernetes CSP agent
configuration. [Refer documentation](../../administratorGuide/manageAccounts/#onboarding-health-status-preview)
- **Added** support for Vulnerability Solutions using AWS Inspector.
Configuring AWS inspector with Common Vulnerability rule packages allows us
to collect all the vulnerabilities associated with each of the EC2
instances. [Refer documentation](../../onboardingGuide/awsVMBaselineConfiguration/)
- **Platform & Stability Improvements**
- Fixed following bugs
- Asset Security dashboard takes long time to load for large accounts
- Duplicate resources and policy mismatch in LinuxVirtualMachine on asset security
- Incorrect Audit log when user disables AWS Config based data collection
- Azure application validity check should be the first entry on Onboarding health status page permissions section
- Incorrect doc link on O365 onboarding health status page
- Control numbers not visible in CSV Report
- Duplicate resources in Azure ADCertificate on asset security
- ResourceTypes are missing on Asset Security
- Missing resources for Blob container policies on Policy details
- Incorrect round off values on Aggregated billing dashboard
- Getting extra benchmarks for in GetBenchmarkList API for Healthcare marketplace license
- Resource search is not working on Asset security dashboard
- Extra comma is visible at the end of CVE id for Vulnerability (Rapid7 and Qualys)
- **Updates to Security Policies & Benchmarks**
- **Updated** policy benchmark mappings for SOC2 - AICPA TSC 2017 for AWS,
Azure, and Office 365 cloud accounts**.**
June 2020 - v3.00.0
-------------------
- **User Experience Improvements**
- **Initial release for** Product branding and logo updates. Various features including Landing pages, Login page, Email notifications etc., were updated to display Zscaler Cloud Security Posture Management (CSPM) branding.
- **Updated** the 'Billing Dashboard page' to allow for a CSV file download detailing utilization information for individual cloud Accounts and aggregated License levels - CSV report.
- **Updated** Detailed Word report to be now download for Private Benchmarks.
- **Updated** the 'Onboarding Health Status' page to now include the pre-requisite checks for Azure Service Principal, M365 Service Principal, and Partner Admin Link (PAL). [Refer documentation](../../administratorGuide/manageAccounts/#onboarding-health-status-preview){target=_blank}.
- **Added** integrations with Rapid7 Azure Vulnerability Solutions. Customers with Rapid7 VA solution on Azure can now visualize Rapid7 reported vulnerabilities on Cloudneeti’s Asset Security Posture dashboard. [Refer documentation](../../onboardingGuide/azureVulnerability/#72-install-vulnerability-solution-on-vms){target=_blank}
- **Platform & Stability Improvements**
- Scale, and stability improvements in data collection and processing by using auto scaling Cloudneeti’s backend databases.
- Fixed following bugs
- AWS CloudTrail policies are not getting remediated in multi-account remediation
- On updating the API App, event type in audit logs displays 'Created' and 'Secret Regenerated for Connected App' instead of 'Updated'
- Incorrect command in Audit procedure for 'Ensure packet redirect sending is disabled' policy
- 'Ensure syslog-ng service is enabled' policy is Pass even if syslog-ng is disabled
- Incorrect remediation procedure for 'Ensure Audit Profile captures all the Activities'
- Incorrect count of AWS OS baseline policies on Onboarding Health status page
- Auto remediation is not working for new RDS resources deployed using script
- 'Windows 2012R2 - Ensure 'Restore files and directories' is set to 'Administrators'' not able to open details page
- When policy details resource table is scrolled horizontally, the cells move horizontally without the header
- Ubuntu 18.04 & CentOS 7 : Second command in Audit procedure are not applicable for mentioned policies
- 'Ubuntu 18.04 - Ensure RDS is disabled' policy is passing even if Audit procedure is not followed completely
- 'Ubuntu 18.04 - Ensure LDAP server is not enabled' policy is failing even if LDAP server is not enabled
- Word report doesn't show manual, pre-requisite and override policies
- Unable to download word report for Azure Marketplace license
- Audit and Remediation procedure not working for "Ensure sticky bit is set on all world-writable directories"
- **Updates to Security Policies & Benchmarks**
- CIS certified Cloudneeti for [Red Hat Enterprise Linux 7](https://www.cisecurity.org/partner/cloudneeti/){target=_blank}
- CIS Red Hat Enterprise Linux 7 Benchmark, v2.2.0, Level 1 - Server
- CIS Red Hat Enterprise Linux 7 Benchmark, v2.2.0, Level 2 - Server
- CIS Red Hat Enterprise Linux 7 Benchmark, v2.2.0, Level 1 - Workstation
- CIS Red Hat Enterprise Linux 7 Benchmark, v2.2.0, Level 2 - Workstation
- **Updated** policy benchmark mappings for PCI DSS 3.2.1 for AWS, Azure, and
Office 365 cloud accounts.
June 2020 - v2.32.1
-------------------
- **User Experience Improvements**
- **Added** new Cloudneeti API: Added the following API’s.
- **GetHealthStatus:** The API provides account health status for given
cloud account. [Refer documentation](../../userGuide/getHealthStatus/){target=_blank}
- **GetLicenseAccounts:** The API provides a list of Cloud Accounts for
given License. [Refer documentation](../../userGuide/getLicenseAccounts/){target=_blank}
- **GetBenchmarkSummary:** The Audit Summary Report API provide information related to your compliance posture across various compliance standards. The filters available through the API enable you to view your status across different cloud accounts and for different benchmarks. [Refer documentation](../../userGuide/getBenchmarkSummary/){target=_blank}
- **Updated** the 'Billing Dashboard page'. This release provides aggregated
billing visibility to the consumed resource capacity. Customers/Partners can
now use the resource consumption data to calculate the monthly/yearly
invoices across all accounts in a license. [Refer documentation](../../administratorGuide/billingDashboard/#aggregated-resource-counts-at-license-level){target=_blank}
- **Updated** the ‘Onboarding Health Status’ page to now includes the accounts
scan quota. It will display a consumed account scan quota along with a total
available quota. [Refer documentation](../../administratorGuide/manageAccounts/#onboarding-health-status-preview){target=_blank}
- **Added** Summary Word report to download the summary report in word format
apart from the existing PDF report [Refer documentation](../../userGuide/reports/#summary-word-report){target=_blank}
- **Platform & Stability Improvements**
- Fixed following bugs
- Resource count incorrect and less policies for: S3 Buckets on Asset security dashboard
- Incorrect Remediation procedure for 'Ensure Audit Profile captures all the Activities'
- Search filters are not working on Onboarding Health status page
- **Updates to Security Policies & Benchmarks**
- CIS certified Cloudneeti for [benchmarks](https://www.cisecurity.org/partner/cloudneeti/){target=_blank}
- CIS Benchmark for Kubernetes v1.5.1, Level 1
- CIS Benchmark for Kubernetes v1.5.1, Level 2
- **Updated** policy benchmark mappings for NIST-CSF for AWS, Azure, and
Office 365 cloud accounts**.**
June 2020 - v2.31.1
-------------------
- **User Experience Improvements**
- **Added** 'Billing Dashboard page'. This release provides billing visibility to the consumed resource capacity. Customers/Partners can now use the resource consumption data to calculate the monthly/yearly invoices. [Refer documentation](../../administratorGuide/billingDashboard/)
- **Updated** 'Onboarding Health Status' page to now include a Customer pre-requisite of Enabling AWS config on their AWS accounts. [Refer documentation](../../onboardingGuide/awsAccountHealthStatus/)
- **Updated** Asset Security for “Total Resources” and “Protected Total
Resources”
- **Platform & Stability Improvements**
- Fixed following bugs
- Getting error on Benchmark summary page when user switch between
accounts before page loads
- Benchmark logo is missing on feature and quotas page for "Center for
Internet Security Microsoft Windows Server 2016 Benchmark v1.0.0
[preview]".
- Few Categories are not visible on the Private Benchmark summary page
even after adding
- **Updates to Security Policies & Benchmarks**
- **Updated** 'Ensure Advanced Threat Protection safe links policy is enabled' policy for M365 is marked as Manual as compliant status not reflecting correct results from Agent.
- **Added** new security benchmark “*Center for Internet Security Microsoft
Windows Server 2016 Benchmark v1.0.0*” for AWS cloud account
- **Added** a new security benchmark “*Unclassified - Naval Nuclear Propulsion
Information (U-NNPI)*” for workloads (includes Cloud Resources, IAM, OS Baselines, Kubernetes clusters) in the following cloud accounts.
- **Azure**
- **AWS**
- **M365**
May 2020 - v2.30.1
-------------------------
1. **User Experience Improvements**
- None
2. **Platform & Stability Improvements**
- **Microsoft Azure**
- Updated Azure Data collection and processing mechanisms to use Azure
Resource Graph API to support massive scale requirements for following
Azure Services.
- Virtual Machine
- Storage Account
- COSMOS DB
- MySQLDatabaseServer
- **Amazon Web Services**
- **New** AWS account onboarding using AWS config: AWS Account onboarding
now supports AWS Config for bulk data collection from AWS accounts. This
change allows customers with large number of cloud resources to be onboarded
to Cloudneeti.
**Details:** [AWS Config](https://aws.amazon.com/config/) enables you to
assess, audit and evaluate configurations of your AWS resources. Using AWS
Config APIs, Cloudneeti will now be able to pull out resource configuration
metadata at scale. This optional onboarding configuration will be used by
default for accounts with larger number of resources. Refer documentation
for more details [here](../../onboardingGuide/awsEnableConfigBasedDataCollection/)
- Updated AWS Data collection and processing mechanisms to use AWS config to
support massive scale requirements for the following AWS services.
- AWS::EC2::Instance
- AWS::EC2::Volume
- AWS::EC2::SecurityGroup
- AWS::S3::Bucket
- **Fixed following bugs**
- AWS k8s benchmark 'CIS K8s v1.5.0' has benchmark logo missing
- Duplicate resources are visible on policy details for 'Ensure that Windows Virtual - Machines are always AD Domain joined'
- 'Enable audit data recording' policy for M365 is marked as Manual even if it is Prerequisite and steps for prereq are also missing in specification
3. **Updates to Security Policies & Benchmarks**
April 2020 - v2.29.1
---------------------------
1. **User Experience Improvements**
- **New Cloudneeti API:** Added API to get a benchmark list for a cloud
account. This API will be useful to get a list of all benchmarks supported
for a given cloud account. Refer documentation for more
details [here](../../userGuide/getSupportedBenchmarks/)
- **New Account onboarding health-status page (Preview) :** Added new page to
display health status of an onboarded cloud account. For customers/partners
managing large number of cloud accounts , the feature provides insights into
the state of your cloud account onboarded to Cloudneeti like missing
permissions, pre-requisites, etc. Refer documentation for more
details [here](../../administratorGuide/manageAccounts/#onboarding-health-status-preview)
- **Updates to AWS Remediation framework:** Releasing new version to AWS
Remediation framework. Includes new sets of auto-remediation policies for
AWS accounts. Existing customer deployments will need to upgraded to the
newwe version of the AWS remediation framework. Refer documentation for more
details [here](../../remediation/awsRemediation/)
- **New Security Policy Status:** Policies that are overridden using the
policy governance features released in v2.28, will now be marked with status
“Policy(O)”, indicating a Pass due to an Override. Refer documentation for
more
details [here](../../gettingStarted/howItWorks/#security-posture)
- Pass(O) – a security policy that is managed over-ride by the customer as
Pass.
- **New Risk Status:** Cloudneeti provides various security policies that are
to be governed manually, either due to no automation being available, or it
might be a related to a process/procedure that can’t be automatically
deduced. As deduction is not automatic, the risk likelihood calculations
mark them as “Undetermined”. This is available on the “Risk” dashboard and
“Cloud Security Best Practices”. Refer documentation for more
details [here](../../gettingStarted/howItWorks/#risk-likelihood)
- Undetermined – security policies with status ‘No Resources’ or ‘Manual’
or ‘Prerequisite’ or ‘Excluded’ are marked with this risk likelihood.
2. **Platform & Stability Improvements**
- Fixed following bugs
- "Ensure that the --insecure-bind-address argument is not set" is
duplicated In Benchmark category Kubernetes - API Server and Kubernetes
- etcd respectively
- Getting 'No resources' even if 'Storage Account Key Operator Service'
role is assigned and storage accounts are also present
- Duplicate manual policies are visible with status Manual and 'No
resources' for private benchmark
3. **Policies & Benchmarks Additions/Updates**
- **Updated policy benchmark mappings for NIST SP 800-53 Rev. 4, ISO/IEC 27001 for AWS, Azure and Office 365 cloud accounts.**
- **Added support for Amazon Elastic Kubernetes Service (Amazon EKS)**:
Cloudneeti includes CIS recommendations for AWS EKS workloads. Customer
would deploy a a Cloudneeti docker agent to EKS Kubernetes Cluster.
Cloudneeti provides automated CIS hardening policies and out-of-box mappings
for all 13+ compliance frameworks included in the product.
Refer documentation for more
details [here](../../onboardingGuide/configureCloudneetiAgentInEKS/)
**April 2020 - v2.28.1**
----------------------------------
1. **User Experience Improvements**
- **Azure Security Center Push Integration (Preview):** The integration between Azure Security Center and Cloudneeti provides a seamless experience to customers in protecting their Azure environments against cyber-threats and mitigating compliance risks. Cloudneeti application will push custom recommendations with assessment data of Azure Cloud Account(s) to Microsoft Azure Security Center. Refer documentation for more details [here](../../administratorGuide/azureASCPushIntegration/){target=_blank}.
- **Override security policy status** : Cloudneeti allows admin users to override the security policy status. After an evaluation of a risk associated to policy compliance, Customers/Auditors can decide on overriding the policy to meet the internal governance needs. Various options to indicate 3rd
party compensating controls, time-bound exceptions to exclude policies are available. Overriding policy status indicates that you have completed resolution and if done without caution, it might carry an inherent security risk. New resolution status will be effective at the cloud account level across all benchmarks post next successful Cloud account scan. Refer documentation for more details [here](../../administratorGuide/overrideSecurityPolicyStatus/){target=_blank}.
- **Added support for Azure Kubernetes Service (AKS)**: Cloudneeti includes and extends Azure Security center recommendations for AKS by deploying a Cloudneeti agent to Azure Kubernetes Cluster. A docker container agent is deployed to collect data for additional security policies. Cloudneeti then provides out-of-box mappings for all 13+ compliance frameworks included in the product. Refer documentation for more details [here](../../onboardingGuide/configureCloudneetiAgentInAKS/){target=_blank}.
- **Security Policy Status:** Added new policy statuses to provide more clarity to the security posture. This helps enterprise customers, MSPs and large risk auditors to conduct continuous security assurance using the Cloudneeti product. Refer documentation for more details [here](../../gettingStarted/howItWorks/#security-posture){target=_blank}.
- Manual – a security policy that is managed manually by the customer.
- Prerequisite – indicates that the policy needs actions by customers, e.g. configure permissions or deploy agents to collect meta-data.
- Excluded – indicates the policy was excluded as part of a policy governance actions.
- Deprecated the “Security” dashboard and added navigation for dashboards (Compliance, Risk, & Assets Security) in the left navigation menu.
2. **Platform & Stability Improvements**
- Fixed following bugs
- "Windows 2012R2 - Ensure 'Restore files and directories' is set to 'Administrators'" not able to open details page.
- Getting 'No resources' even if 'Storage Contributor' role is assigned and storage accounts are also present.
3. **Policies & Benchmarks Additions/Updates**
**March 2020 - v2.27.1**
----------------------------------
1. **User Experience Improvements**
- Cloudneeti API access: Cloudneeti exposes API to access for Cloud Account
onboarding, audit report, scan etc . Refer documentation for more details
[here](../../userGuide/restAPIs/)
- Added *“Asset Security (Preview)”* dashboard: View protected Azure and AWS
assets per region. Refer documentation for more
details [here](../../userGuide/dashboards/#assets-security-preview).
Added vulnerabilities for Azure VM
- Deprecated “Assets” dashboard
- Private Benchmarks: restrict user deletion, role changes in case
collaborated.
- Updates in benchmark sequence on “*Compliance*” dashboard.
2. **Platform & Stability Improvements**
- Fixed following bugs
- Audit log not showing Initiated by when user tries to remediate
AWS/Azure policy.
- Updated implementation for following policies
- Ensure that Logging is enabled for Azure Key Vault
- Ensure that Service Principal Certificates are renewed before it expires
- Audit and Remediation procedures commands are not properly given in the
below policies.
- Ensure discretionary access control permission modification events are
collected
- Ensure unsuccessful unauthorized file access attempts are collected
- Ensure successful file system mounts are collected
- Ensure file deletion events by users are collected
- Ensure changes to system administration scope (sudoers) is collected
- Ensure kernel module loading and unloading is collected
- Ensure events that modify date and time information are collected
- Ensure events that modify user/group information are collected
- Ensure events that modify the system's network environment are collected
- Ensure login and logout events are collected
- Ensure session initiation information is collected
- Ensure Storage Container storing activity logs is not Publicly
accessible
- 'Ensure that monitoring of unencrypted SQL databases is enabled in ASC
3. **Policies & Benchmarks Additions/Updates**
**February 2020 - v2.26.1**
----------------------------------
1. **User Experience Improvements**
- **Asset Security Dashboard Preview**: View protected Azure and AWS assets
per region. Refer documentation for more details [here](../../userGuide/dashboards/#assets-security-preview).
- **Risk Dashboard**: Updates to user interface.
- **Release Notification:** Users will be notified on a new Cloudneeti SaaS release.
- **AWS Remediation:** Support for deploying Cloudneeti Remediation Framework in selected
region.
- **Auto Remediation:** Added audit logs for successful configuration of Azure and AWS auto remediation.
2. **Platform & Stability Improvements**
- Fixed following bugs
- Subsequent AWS resources should get remediated in case one of the resources remediation fails from AWS
- Authentication token enhancements
3. **Policies & Benchmarks Additions/Updates**
- Added following 18 M365 IAM policies
To get data for these policies, please provide version 1.4 while executing the script for upgrade or creation of Office 365 advance security configuration.
- References
- [Upgrading the existing Office 365 account](../../onboardingGuide/office365AdvanceSecurityConfigurationUpgrade)
- [Onboarding new Office 365 account](../../onboardingGuide/office365Subscription/) and [Creation of Advanced security configurations.](../../onboardingGuide/office365Subscription/#step-3-advanced-security-configurations)
**Added following 63 new security policies for GCP cloud account**
| Category Name | Policy Name | |--------------------------------------|----------------------------------------------------------------------------------------------------------------------------| | GCP - Identity and Access Management | Ensure that corporate login credentials are used | | GCP - Identity and Access Management | Ensure that multi-factor authentication is enabled for all non-service accounts | | GCP - Identity and Access Management | Ensure that there are only GCP-managed service account keys for each service account | | GCP - Identity and Access Management | Ensure that Service Account has no Admin privileges | | GCP - Identity and Access Management | Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at project level | | GCP - Identity and Access Management | Ensure user-managed/external keys for service accounts are rotated every 90 days or less | | GCP - Identity and Access Management | Ensure that Cloud KMS cryptokeys are not anonymously or publicly accessible | | GCP - Identity and Access Management | Ensure KMS encryption keys are rotated within a period of 90 days | | GCP - Identity and Access Management | Ensure API keys are restricted to use by only specified Hosts and Apps | | GCP - Identity and Access Management | Ensure API keys are restricted to only APIs that application needs access | | GCP - Identity and Access Management | Ensure that corporate login credentials are used | | GCP - Identity and Access Management | Ensure that Security Key Enforcement is enabled for all admin accounts | | GCP - Identity and Access Management | Ensure that Separation of duties is enforced while assigning service account related roles to users | | GCP - Identity and Access Management | Ensure that Separation of duties is enforced while assigning KMS related roles to users | | GCP - Identity and Access Management | Ensure API keys are not created for a project | | GCP - Logging and Monitoring | Ensure that Cloud Audit Logging is configured properly across all services and all users from a project | | GCP - Logging and Monitoring | Ensure that sinks are configured for all log entries | | GCP - Logging and Monitoring | Ensure that retention policies on log buckets are configured using Bucket Lock | | GCP - Logging and Monitoring | Ensure log metric filter and alerts exist for project ownership assignments/changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for Audit Configuration changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for Custom Role changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for VPC Network Firewall rule changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for VPC network route changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for VPC network changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for Cloud Storage IAM permission changes | | GCP - Logging and Monitoring | Ensure that the log metric filter and alerts exist for SQL instance configuration changes | | GCP - Networking | Ensure that the default network does not exist in a project | | GCP - Networking | Ensure legacy networks do not exist for a project | | GCP - Networking | Ensure that DNSSEC is enabled for Cloud DNS | | GCP - Networking | Ensure that RSASHA1 is not used for the key-signing key in Cloud DNS DNSSEC | | GCP - Networking | Ensure that RSASHA1 is not used for the zone-signing key in Cloud DNS DNSSEC | | GCP - Networking | Ensure that SSH access is restricted from the internet | | GCP - Networking | Ensure that RDP access is restricted from the Internet | | GCP - Networking | Ensure that VPC Flow Logs is enabled for every subnet in a VPC Network | | GCP - Networking | Ensure no HTTPS or SSL proxy load balancers permit SSL policies with weak cipher suites | | GCP - Compute | Ensure that instances are not configured to use the default service account | | GCP - Compute | Ensure that instances are not configured to use the default service account with full access to all Cloud APIs | | GCP - Compute | Ensure "Block Project-wide SSH keys" is enabled for VM instances | | GCP - Compute | Ensure oslogin is enabled for a Project | | GCP - Compute | Ensure "Enable connecting to serial ports" is not enabled for VM Instance | | GCP - Compute | Ensure that IP forwarding is not enabled on Instances | | GCP - Compute | Ensure VM disks for critical VMs are encrypted with Customer-Supplied Encryption Keys | | GCP - Compute | Ensure Compute instances are launched with Shielded VM enabled | | GCP - Compute | Ensure that Compute instances do not have public IP addresses | | GCP - Compute | Ensure that App Engine applications enforce HTTPS connections | | GCP - Storage and Database | Ensure that Cloud Storage bucket is not anonymously or publicly accessible | | GCP - Storage and Database | Ensure that Cloud Storage buckets have uniform bucket-level access enabled | | GCP - Storage and Database | Ensure that the Cloud SQL database instance requires all incoming connections to use SSL | | GCP - Storage and Database | Ensure that Cloud SQL database instances are not open to the world | | GCP - Storage and Database | Ensure that Cloud SQL database instances do not have public IPs | | GCP - Storage and Database | Ensure that Cloud SQL database instances are configured with automated backups | | GCP - Storage and Database | Ensure that a MySQL database instance does not allow anyone to connect with administrative privileges | | GCP - Storage and Database | Ensure that the 'local_infile' database flag for a Cloud SQL Mysql instance is set to 'off' | | GCP - Storage and Database | Ensure that the 'log_checkpoints' database flag for Cloud SQL PostgreSQL instance is set to 'on' | | GCP - Storage and Database | Ensure that the 'log_connections' database flag for Cloud SQL PostgreSQL instance is set to 'on' | | GCP - Storage and Database | Ensure that the 'log_disconnections' database flag for Cloud SQL PostgreSQL instance is set to 'on' | | GCP - Storage and Database | Ensure that the 'log_lock_waits' database flag for Cloud SQL PostgreSQL instance is set to 'on' | | GCP - Storage and Database | Ensure that the 'log_min_messages' database flag for Cloud SQL PostgreSQL instance is set appropriately | | GCP - Storage and Database | Ensure that the 'log_temp_files' database flag for Cloud SQL PostgreSQL instance is set to '0' (on) | | GCP - Storage and Database | Ensure that the 'log_min_duration_statement' database flag for Cloud SQL PostgreSQL instance is set to '-1' (disabled) | | GCP - Storage and Database | Ensure that the 'cross db ownership chaining' database flag for Cloud SQL SQL Server instance is set to 'off' | | GCP - Storage and Database | Ensure that the 'contained database authentication' database flag for Cloud SQL on the SQL Server instance is set to 'off' | | GCP - Storage and Database | Ensure that BigQuery datasets are not anonymously or publicly accessible |Deprecated following 5 policies for K8s baseline as data from Cloud Service Provider API is deprecated
| **Category** | **Policy Title** | Connector Type | |------------------------------------------------------------|----------------------------------------------------------------------------------------------------|----------------| | Kubernetes - Control Plane Components - API Server | VM Hosted - Ensure that the --encryption-provider-config argument is set as appropriate | Azure | | Kubernetes - Control Plane Components - Controller Manager | VM Hosted - Ensure that the --terminated-pod-gc-threshold argument is set as appropriate | Azure | | Kubernetes - Control Plane Components - API Server | AKS Engine - Ensure that the --encryption-provider-config argument is set as appropriate | Azure | | Kubernetes - Control Plane Components - API Server | EC2-Instance Hosted - Ensure that the --encryption-provider-config argument is set as appropriate | AWS | | Kubernetes - Control Plane Components - Controller Manager | EC2-Instance Hosted - Ensure that the --terminated-pod-gc-threshold argument is set as appropriate | AWS |Deprecated following 2 policies for AWS as additional check needs to added as per API response
| **Category** | **Policy Title** | |--------------------------------------|------------------------------------------------------| | AWS - Audit and Logging | Ensure Global resources are included into Amazon Config service configuration | | AWS - Identity and Access Management | Ensure you do not allow unknown cross account access via permission policies to AWS Lambda functions |Added the following 8 API Gateway resource - related policies for the AWS account.
| **Category** | **Policy Title** | |-----------------------------|-------------------------------------------------------------------------------------------------------------------------------------------| | AWS - Audit and Logging | Ensure that CloudWatch Log feature is enabled for Amazon API Gateway | | AWS - Audit and Logging | Ensure that Detailed CloudWatch Metrics feature is enabled for Amazon API Gateway | | AWS - Compute | Ensure that AWS X-Ray Tracing feature is enabled for Amazon API Gateway | | AWS - Data Protection | Ensure that SSL certificates attached with Amazon API Gateway to verify HTTP requests made to backend system are from API Gateway service | | AWS - Storage and Databases | Ensure that Content Encoding feature is enabled for Amazon API Gateway APIs | | AWS - Networking | Ensure that Amazon API Gateway APIs accessible only through private API endpoints | | AWS - Data Protection | Ensure that API Gateway client-side SSL certificate is renewed before expiration | | AWS - Networking | Ensure that AWS WAF is integrated with Amazon API Gateway to protect APIs from common web exploits |Added the following 193 OS hardening policies for Windows Server 2019 server hosted in an Azure cloud account
| **Category name** | **Policy Title** | |-----------------------------|----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------| | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Group Membership' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Authentication Policy Change' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Other Object Access Events' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit MPSSVC Rule-Level Policy Change' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Account Lockout' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Logon' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Credential Validation' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit System Integrity' is set to 'Success and Failure | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Special Logon' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit PNP Activity' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Logoff' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit User Account Management' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Security System Extension' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Security State Change' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Security Group Management' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Removable Storage' is set to 'Success and Failure' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Process Creation' is set to 'Success' | | Win OS-19 - Audit Policy | Windows 2019 - Ensure 'Audit Audit Policy Change' is set to 'Success and Failure' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network server: Amount of idle time required before suspending session' is set to '15 or fewer minute(s), but not 0' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network client: Send unencrypted password to third-party SMB servers' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network client: Digitally sign communications (always)' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network server: Digitally sign communications (if client agrees)' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Interactive logon: Do not display last user name' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Include command line in process creation events' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Disallow Digest authentication' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Prohibit installation and configuration of Network Bridge on your DNS domain network' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Prohibit use of Internet Connection Sharing on your DNS domain network' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Require secure RPC communication' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Set client connection encryption level' is set to 'Enabled: High Level' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Always prompt for password upon connection' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow input personalization' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow indexing of encrypted files' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow Cortana' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow Cortana above lock screen' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Accounts: Limit local account use of blank passwords to console logon only' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Enable 'Turn on behavior monitoring' | | Win OS-19 - Registry Policy | Windows 2019 - Enable 'Send file samples when further analysis is required' for 'Send Safe Samples' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not display the password reveal button' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Scan removable drives' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Search Service' is configured | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Configure SMB v1 server' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Configure local setting override for reporting to Microsoft MAPS' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Devices: Allow undock without having to log on' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Detect change from default RDP port' is configured | | Win OS-19 - Registry Policy | Windows 2019 - Configure 'Network access: Remotely accessible registry paths and sub-paths' | | Win OS-19 - Registry Policy | Windows 2019 - Configure 'Network access: Remotely accessible registry paths' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network client: Digitally sign communications (if server agrees)' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Disallow Autoplay for non-volume devices' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Enable RPC Endpoint Mapper Client Authentication' is set to 'Enabled' (MS only) | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Enable insecure guest logons' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not use temporary folders per session' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not show feedback notifications' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not display network selection UI' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not delete temp folders upon exit' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Do not allow passwords to be saved' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Disallow WinRM from storing RunAs credentials' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Enumerate administrator accounts on elevation' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Configure Solicited Remote Assistance' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv2 session security, Require 128-bit encryption' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Prevent downloading of enclosures' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Prevent enabling lock screen camera' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Prevent enabling lock screen slide show' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow Basic authentication' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv2 session security, Require 128-bit encryption' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: LDAP client signing requirements' is set to 'Negotiate signing' or higher | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM & NTLM' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network Security: Configure encryption types allowed for Kerberos' is set to 'RC4_HMAC_MD5, AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow' (MS only) | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled' (MS only) | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled' (MS only) | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Minimize the number of simultaneous connections to the Internet or a Windows Domain' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network server: Disconnect clients when logon hours expire' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Devices: Prevent users from installing printer drivers' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Devices: Allowed to format and eject removable media' is set to 'Administrators' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Continue experiences on this device' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Configure Offer Remote Assistance' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Enable Windows NTP Client' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Block user from showing account details on sign-in' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Interactive logon: Do not require CTRL+ALT+DEL' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Boot-Start Driver Initialization Policy' is set to 'Enabled: Good, unknown and bad but critical' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Configure Windows Defender SmartScreen' is set to 'Enabled: Warn and prevent bypass' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Microsoft network server: Digitally sign communications (always)' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Always install with elevated privileges' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow user control over installs' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow unencrypted traffic' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow Telemetry' is set to 'Enabled: 0 - Security [Enterprise Only]' or 'Enabled: 1 - Basic' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow search and Cortana to use location' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Allow Microsoft accounts to be optional' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off Autoplay' is set to 'Enabled: All drives' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'System objects: Strengthen default permissions of internal system objects (e.g. Symbolic Links)' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'System objects: Require case insensitivity for non-Windows subsystems' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Sign-in last interactive user automatically after a system-initiated restart' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Shutdown: Allow system to be shut down without having to log on' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Private: Allow unicast response' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Domain: Allow unicast response' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Shutdown: Clear virtual memory pagefile' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Set the default behavior for AutoRun' is set to 'Enabled: Do not execute any autorun commands' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Require user authentication for remote connections by using Network Level Authentication' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Allow unicast response' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Recovery console: Allow floppy copy and access to all drives and all folders' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Settings: Display a notification' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Settings: Apply local firewall rules' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Settings: Apply local connection security rules' is set to 'Yes' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Domain: Firewall state' is set to 'On (recommended)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Outbound connections' is set to 'Allow (default)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'System settings: Use Certificate Rules on Windows Executables for Software Restriction Policies' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Public: Firewall state' is set to 'On (recommended)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Private: Settings: Display a notification' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Private: Outbound connections' is set to 'Allow (default)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Private: Firewall state' is set to 'On (recommended)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Detect application installations and prompt for elevation' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Domain: Outbound connections' is set to 'Allow (default)' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Specify the interval to check for definition updates' is set to 'Enabled:1' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Virtualize file and registry write failures to per-user locations' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Run all administrators in Admin Approval Mode' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off app notifications on the lock screen' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Only elevate UIAccess applications that are installed in secure locations' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Switch to the secure desktop when prompting for elevation' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off shell protocol protected mode' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Windows Firewall: Domain: Settings: Display a notification' is set to 'No' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off multicast name resolution' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off Data Execution Prevention for Explorer' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Behavior of the elevation prompt for standard users' is set to 'Automatically deny elevation requests' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode' is set to 'Prompt for consent on the secure desktop' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'User Account Control: Admin Approval Mode for the Built-in Administrator account' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn on convenience PIN sign-in' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off Microsoft consumer experiences' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off Internet Connection Wizard if URL connection is referring to Microsoft.com' is set to 'Enabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off heap termination on corruption' is set to 'Disabled' | | Win OS-19 - Registry Policy | Windows 2019 - Ensure 'Turn off downloading of print drivers over HTTP' is set to 'Enabled' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Password must meet complexity requirements' is set to 'Enabled' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Modify an object label' is set to 'No One' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Create permanent shared objects' is set to 'No One' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Maximum password age' is set to '70 or fewer days, but not 0' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Shut down the system' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Deny log on as a batch job' to include 'Guests' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Access Credential Manager as a trusted caller' is set to 'No One' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Manage auditing and security log' is set to 'Administrators' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Enable computer and user accounts to be trusted for delegation' is set to 'No One' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Minimum password length' is set to '14 or more character(s)' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Load and unload device drivers' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Create symbolic links' is set to 'Administrators, NT VIRTUAL MACHINE\Virtual Machines' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Allow log on through Remote Desktop Services' is set to 'Administrators, Remote Desktop Users' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Allow log on locally' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Access this computer from the network' is set to 'Administrators, Authenticated Users, ENTERPRISE DOMAIN CONTROLLERS' (DC only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Increase scheduling priority' is set to 'Administrators, Window Manager\Window Manager Group' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Generate security audits' is set to 'LOCAL SERVICE, NETWORK SERVICE' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Take ownership of files or other objects' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Store passwords using reversible encryption' is set to 'Disabled' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Change the system time' is set to 'Administrators, LOCAL SERVICE' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Change the time zone' is set to 'Administrators, LOCAL SERVICE' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Create a pagefile' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Create a token object' is set to 'No One' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Create global objects' is set to 'Administrators, LOCAL SERVICE, NETWORK SERVICE, SERVICE' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Increase a process working set' is set to 'Usres' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Deny log on as a service' to include 'Guests' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Deny log on locally' to include 'Guests' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Enforce password history' is set to '24 or more password(s)' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Force shutdown from a remote system' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Minimum password age' is set to '1 or more day(s)' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Lock pages in memory' is set to 'No One' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Back up files and directories' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Accounts: Guest account status' is set to 'Disabled' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Replace a process level token' is set to 'LOCAL SERVICE, NETWORK SERVICE' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Perform volume maintenance tasks' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Profile single process' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Profile system performance' is set to 'Administrators, NT SERVICE\WdiServiceHost' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Restore files and directories' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Modify firmware environment values' is set to 'Administrators' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Deny access to this computer from the network' to include 'Guests, Local account and member of Administrators group' (MS only) | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Deny log on through Remote Desktop Services' is set to 'Guests, Local account' | | Win OS-19 - Security Policy | Windows 2019 - Ensure 'Act as part of the operating system' is set to 'No One' |Deprecated following 30 policies for OS baseline for Windows-2016 server as data from Microsoft API is deprecated
| **Category** | **Policy Title** | |--------------------------|--------------------------------------------------------------------| | Win OS-16 - Audit Policy | Ensure 'Audit Application Group Management' is set | | Win OS-16 - Audit Policy | Ensure 'Audit IPsec Driver' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Other System Events' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Authorization Policy Change' is set to 'Success' | | Win OS-16 - Audit Policy | Audit IPsec Extended Mode | | Win OS-16 - Audit Policy | Audit Detailed File Share | | Win OS-16 - Audit Policy | Audit Filtering Platform Packet Drop | | Win OS-16 - Audit Policy | Audit Kernel Object | | Win OS-16 - Audit Policy | Audit IPsec Main Mode | | Win OS-16 - Audit Policy | Audit File Share | | Win OS-16 - Audit Policy | Audit IPsec Quick Mode | | Win OS-16 - Audit Policy | Audit Filtering Platform Policy Change | | Win OS-16 - Audit Policy | Audit Handle Manipulation | | Win OS-16 - Audit Policy | Audit Network Policy Server | | Win OS-16 - Audit Policy | Audit Central Access Policy Staging | | Win OS-16 - Audit Policy | Audit Other Account Logon Events | | Win OS-16 - Audit Policy | Audit Non Sensitive Privilege Use | | Win OS-16 - Audit Policy | Audit Filtering Platform Connection | | Win OS-16 - Audit Policy | Audit Application Generated | | Win OS-16 - Audit Policy | Audit DPAPI Activity | | Win OS-16 - Audit Policy | Audit File System | | Win OS-16 - Audit Policy | Audit User/Device Claims | | Win OS-16 - Audit Policy | Audit Policy: Detailed Tracking: Process Termination | | Win OS-16 - Audit Policy | Audit Policy: Logon-Logoff: IPsec Main Mode | | Win OS-16 - Audit Policy | Audit Process Termination | | Win OS-16 - Audit Policy | Audit SAM | | Win OS-16 - Audit Policy | Audit Registry | | Win OS-16 - Audit Policy | Audit Other Policy Change Events | | Win OS-16 - Audit Policy | Audit Other Privilege Use Events | | Win OS-16 - Audit Policy | Audit RPC Events |Deprecated following 30 policies for OS baseline for Windows-2012 R2 server as data from Microsoft API is deprecated
| **Category** | **Policy Title** | |----------------------------|----------------------------------------------------------------| | Win OS-12R2 - Audit Policy | Ensure 'Audit Application Group Management' is set | | Win OS-12R2 - Audit Policy | Ensure 'Audit Authorization Policy Change' is set to 'Success' | | Win OS-12R2 - Audit Policy | Audit Policy: System: IPsec Driver | | Win OS-12R2 - Audit Policy | Audit Policy: System: Other System Events | | Win OS-12R2 - Audit Policy | Audit Central Access Policy Staging | | Win OS-12R2 - Audit Policy | Audit Handle Manipulation | | Win OS-12R2 - Audit Policy | Audit Kernel Object | | Win OS-12R2 - Audit Policy | Audit File System | | Win OS-12R2 - Audit Policy | Audit Detailed File Share | | Win OS-12R2 - Audit Policy | Audit Filtering Platform Packet Drop | | Win OS-12R2 - Audit Policy | Audit Non Sensitive Privilege Use | | Win OS-12R2 - Audit Policy | Audit Network Policy Server | | Win OS-12R2 - Audit Policy | Audit File Share | | Win OS-12R2 - Audit Policy | Audit IPsec Main Mode | | Win OS-12R2 - Audit Policy | Audit IPsec Quick Mode | | Win OS-12R2 - Audit Policy | Audit Filtering Platform Policy Change | | Win OS-12R2 - Audit Policy | Audit Filtering Platform Connection | | Win OS-12R2 - Audit Policy | Audit Application Generated | | Win OS-12R2 - Audit Policy | Audit IPsec Extended Mode | | Win OS-12R2 - Audit Policy | Audit DPAPI Activity | | Win OS-12R2 - Audit Policy | Audit Other Privilege Use Events | | Win OS-12R2 - Audit Policy | Audit Other Account Logon Events | | Win OS-12R2 - Audit Policy | Audit Policy: Detailed Tracking: Process Termination | | Win OS-12R2 - Audit Policy | Audit RPC Events | | Win OS-12R2 - Audit Policy | Audit Registry | | Win OS-12R2 - Audit Policy | Audit User/Device Claims | | Win OS-12R2 - Audit Policy | Audit Policy: Logon-Logoff: IPsec Main Mode | | Win OS-12R2 - Audit Policy | Audit Other Policy Change Events | | Win OS-12R2 - Audit Policy | Audit Process Termination | | Win OS-12R2 - Audit Policy | Audit SAM |Added the following 10 policies for S3 and Networking resource-related policies for the AWS account.
| **Category** | **Policy Title** | |-----------------------------|----------------------------------------------------------------------------------------------------------------------------------------------------------| | AWS - Networking | Ensure that Data Trace logging is enabled for WebSocket APIs | | AWS - Networking | Ensure that Access logging is enabled for WebSocket APIs | | AWS - Networking | Ensure that Access-Control-Allow-Origin is not set to all sources for HTTP APIs | | AWS - Networking | Ensure that Access-Control-Allow-Methods is set to specific methods and not * for HTTP APIs | | AWS - Networking | Ensure that Access-Control-Allow-Headers is set to specific Header and not * for HTTP APIs | | AWS - Networking | Ensure that Access-Control-Allow-Credentials is set to True for HTTP APIs | | AWS - Storage and Databases | Ensure that Block public access to buckets and objects granted through new access control lists (ACLs) is turned on for S3 buckets | | AWS - Storage and Databases | Ensure that Block public access to buckets and objects granted through any access control lists (ACLs) is turned on for S3 buckets | | AWS - Storage and Databases | Ensure that Block public access to buckets and objects granted through new public bucket or access point policies is turned on for S3 buckets | | AWS - Storage and Databases | Ensure that Block public and cross-account access to buckets and objects through any public bucket or access point policies are turned on for S3 buckets |Added the following 9 ASG resource-related policies for the AWS account.
| **Category** | **Policy Title** | |---------------------------|----------------------------------------------------------------------------------------------------| | AWS - Business Continuity | Ensure that autoscaling group has a healthcheck type set to ELB | | AWS - Business Continuity | Ensure that termination policy for instances in an ASG is in place | | AWS - Business Continuity | Ensure that MaxInstanceLifetime of instances in an ASG is set | | AWS - Business Continuity | Ensure that DeleteOnTermination is enabled for EBS volumes in ASG launch configurations | | AWS - Audit and Logging | Ensure that Cloudwatch detailed monitoring is enabled in ASG launch configurations | | AWS - Data Protection | Ensure that encrypted EBS volume is being used in ASG launch configurations | | AWS - Compute | Ensure that EBS optimized instances are launched using ASG launch configurations | | AWS - Networking | Ensure that security group in ASG launch configuration does not have SSH port open to the internet | | AWS - Networking | Ensure that security group in ASG launch configuration does not have RDP port open to the internet |Added the following 183 OS hardening policies for Windows Server 2016 server hosted in an AWS cloud account
| **Category** | **Policy Title** | |-----------------------------|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------| | Win OS-16 - Registry Policy | Ensure 'Add workstations to domain' is set to 'Administrators' (DC only) | | Win OS-16 - Registry Policy | Ensure 'Impersonate a client after authentication' is set to 'Administrators, LOCAL SERVICE, NETWORK SERVICE, SERVICE' (DC only) | | Win OS-16 - Registry Policy | Ensure 'Synchronize directory service data' is set to 'No One' (DC only) | | Win OS-16 - Registry Policy | Ensure 'Adjust memory quotas for a process' is set to 'Administrators, LOCAL SERVICE, NETWORK SERVICE' | | Win OS-16 - Registry Policy | Ensure 'Create symbolic links' is set to 'Administrators, NT VIRTUAL MACHINE\Virtual Machines' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Debug programs' is set to 'Administrators' | | Win OS-16 - Audit Policy | Ensure 'Deny access to this computer from the network' is set to 'Guests, Local account and member of Administrators group' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Impersonate a client after authentication' is set to 'Administrators, LOCAL SERVICE, NETWORK SERVICE, SERVICE' and (when the Web Server (IIS) Role with Web Services Role Service is installed) 'IIS_IUSRS' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Log on as a batch job' is set to 'Administrators' (DC Only) | | Win OS-16 - Registry Policy | Ensure 'Network access: Do not allow storage of passwords and credentials for network authentication' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Account lockout duration' is set to '15 or more minute(s)' | | Win OS-16 - Registry Policy | Ensure 'Account lockout threshold' is set to '10 or fewer invalid logon attempt(s), but not 0' | | Win OS-16 - Registry Policy | Ensure 'Reset account lockout counter after' is set to '15 or more minute(s)' | | Win OS-16 - Registry Policy | Ensure 'Enable screen saver' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Force specific screen saver: Screen saver executable name' is set to 'Enabled: scrnsave.scr' | | Win OS-16 - Registry Policy | Ensure 'Password protect the screen saver' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Screen saver timeout' is set to 'Enabled: 900 seconds or fewer, but not 0' | | Win OS-16 - Registry Policy | Ensure 'Turn off toast notifications on the lock screen' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not preserve zone information in file attachments' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Notify antivirus programs when opening attachments' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Windows spotlight on lock screen' is set to Disabled' | | Win OS-16 - Registry Policy | Ensure 'Do not suggest third-party content in Windows spotlight' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Prevent users from sharing files within their profile' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Help Experience Improvement Program' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not use diagnostic data for tailored experiences' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off all Windows spotlight features' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Prevent Codec Download' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not use diagnostic data for tailored experiences' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow password expiration time longer than required by policy' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Enable Local Admin Password Management' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Password Settings: Password Complexity' is set to 'Enabled: Large letters + small letters + numbers + special characters' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Password Settings: Password Length' is set to 'Enabled: 15 or more' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Password Settings: Password Age (Days)' is set to 'Enabled: 30 or fewer' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Apply UAC restrictions to local accounts on network logons' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Configure SMB v1 client driver' is set to 'Enabled: Disable driver' | | Win OS-16 - Registry Policy | Ensure 'Configure SMB v1 server' is set to 'Disabled' | | Win OS-16 - Audit Policy | Ensure 'Enable Structured Exception Handling Overwrite Protection (SEHOP)' is set to 'Enabled' | | Win OS-16 - Audit Policy | Ensure 'Turn on Windows Defender protection against Potentially Unwanted Applications' is set to 'Enabled' | | Win OS-16 - Audit Policy | Ensure 'WDigest Authentication' is set to 'Disabled' | | Win OS-16 - Audit Policy | Ensure 'MSS: (AutoAdminLogon) Enable Automatic Logon (not recommended)' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'MSS: (DisableIPSourceRouting IPv6) IP source routing protection level (protects against packet spoofing)' is set to 'Enabled: Highest protection, source routing is completely disabled' | | Win OS-16 - Audit Policy | Ensure 'MSS: (DisableIPSourceRouting) IP source routing protection level (protects against packet spoofing)' is set to 'Enabled: Highest protection, source routing is completely disabled' | | Win OS-16 - Audit Policy | Ensure 'MSS: (EnableICMPRedirect) Allow ICMP redirects to override OSPF generated routes' is set to 'Disabled' | | Win OS-16 - Audit Policy | Ensure 'MSS: (NoNameReleaseOnDemand) Allow the computer to ignore NetBIOS name release requests except from WINS servers' is set to 'Enabled' | | Win OS-16 - Audit Policy | Ensure 'MSS: (SafeDllSearchMode) Enable Safe DLL search mode (recommended)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'MSS: (ScreenSaverGracePeriod) The time in seconds before the screen saver grace period expires (0 recommended)' is set to 'Enabled: 5 or fewer seconds' | | Win OS-16 - Registry Policy | Ensure 'MSS: (WarningLevel) Percentage threshold for the security event log at which the system will generate a warning' is set to 'Enabled: 90% or less' | | Win OS-16 - Audit Policy | Set 'NetBIOS node type' to 'P-node' (Ensure NetBT Parameter 'NodeType' is set to '0x2 (2)') | | Win OS-16 - Audit Policy | Ensure 'Require domain users to elevate when setting a network's location' is set to 'Enabled' | | Win OS-16 - Audit Policy | Ensure 'Hardened UNC Paths' is set to 'Enabled, with "Require Mutual Authentication" and "Require Integrity" set for all NETLOGON and SYSVOL shares' | | Win OS-16 - Audit Policy | Ensure 'Remote host allows delegation of non-exportable credentials' is set to 'Enabled' | | Win OS-16 - Audit Policy | Ensure 'Configure registry policy processing: Do not apply during periodic background processing' is set to 'Enabled: FALSE' | | Win OS-16 - Audit Policy | Ensure 'Configure registry policy processing: Process even if the Group Policy objects have not changed' is set to 'Enabled: TRUE' | | Win OS-16 - Audit Policy | Ensure 'Turn off background refresh of Group Policy' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Internet download for Web publishing and online ordering wizards' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off printing over HTTP' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not enumerate connected users on domain-joined computers' is set to 'Enabled' | | Win OS-16 - Security Policy | Ensure 'Enumerate local users on domain-joined computers' is set to 'Disabled' (MS only) | | Win OS-16 - Security Policy | Ensure 'Turn off picture password sign-in' is set to 'Enabled' | | Win OS-16 - Security Policy | Ensure 'Untrusted Font Blocking' is set to 'Enabled: Block untrusted fonts and log events' | | Win OS-16 - Registry Policy | Ensure 'Require a password when a computer wakes (on battery)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Require a password when a computer wakes (plugged in)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure enhanced anti-spoofing' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Require pin for pairing' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Disable pre-release features or settings' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Toggle user control over Insider builds' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Block all consumer Microsoft account user authentication' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Prevent the usage of OneDrive for file storage' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow drive redirection' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Windows Defender AntiVirus' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure local setting override for reporting to Microsoft MAPS' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on behavior monitoring' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Scan removable drives' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on e-mail scanning' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Attack Surface Reduction rules' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Attack Surface Reduction rules: Set the state for each ASR rule' is 'configured' | | Win OS-16 - Registry Policy | Ensure 'Prevent users and apps from accessing dangerous websites' is set to 'Enabled: Block' | | Win OS-16 - Registry Policy | Ensure 'Prevent users from modifying settings' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow Windows Ink Workspace' is set to 'Enabled: On, but disallow access above lock' OR 'Disabled' but not 'Enabled: On' | | Win OS-16 - Registry Policy | Ensure 'Turn on PowerShell Script Block Logging' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on PowerShell Transcription' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Automatic Updates' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Automatic Updates: Scheduled install day' is set to '0 - Every day' | | Win OS-16 - Registry Policy | Ensure 'No auto-restart with logged on users for scheduled automatic updates installations' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Manage preview builds' is set to 'Enabled: Disable preview builds' | | Win OS-16 - Registry Policy | Ensure 'Select when Preview Builds and Feature Updates are received' is set to 'Enabled: Semi-Annual Channel, 180 or more days' | | Win OS-16 - Registry Policy | Ensure 'Select when Quality Updates are received' is set to 'Enabled: 0 days' | | Win OS-16 - Registry Policy | Ensure 'Allow Online Tips' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'MSS: (KeepAliveTime) How often keep-alive packets are sent in milliseconds' is set to 'Enabled: 300,000 or 5 minutes (recommended)' | | Win OS-16 - Registry Policy | Ensure 'MSS: (PerformRouterDiscovery) Allow IRDP to detect and configure Default Gateway addresses (could lead to DoS)' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'MSS: (TcpMaxDataRetransmissions IPv6) How many times unacknowledged data is retransmitted' is set to 'Enabled: 3' | | Win OS-16 - Registry Policy | Ensure 'MSS: (TcpMaxDataRetransmissions) How many times unacknowledged data is retransmitted' is set to 'Enabled: 3' | | Win OS-16 - Registry Policy | Ensure 'Enable Font Providers' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on Mapper I/O (LLTDIO) driver' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on Responder (RSPNDR) driver' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Microsoft Peer-to-Peer Networking Services' is set to 'Enabled' | | Win OS-16 - Registry Policy | Disable IPv6 (Ensure TCPIP6 Parameter 'DisabledComponents' is set to '0xff (255)') | | Win OS-16 - Registry Policy | Ensure 'Configuration of wireless settings using Windows Connect Now' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Prohibit access of the Windows Connect Now wizards' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off handwriting personalization data sharing' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off handwriting recognition error reporting' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Registration if URL connection is referring to Microsoft.com' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Search Companion content file updates' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off the "Order Prints" picture task' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off the "Publish to Web" task for files and folders' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off the Windows Messenger Customer Experience Improvement Program' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Windows Customer Experience Improvement Program' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Windows Error Reporting' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Support device authentication using certificate' is set to 'Enabled: Automatic' | | Win OS-16 - Registry Policy | Ensure 'Disallow copying of user input methods to the system account for sign-in' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow network connectivity during connected-standby (on battery)' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow network connectivity during connected-standby (plugged in)' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft Support Diagnostic Tool: Turn on MSDT interactive communication with support provider' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Enable/Disable PerfTrack' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off the advertising ID' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow a Windows app to share application data between users' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow Use of Camera' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Authenticated Proxy usage for the Connected User Experience and Telemetry service' is set to 'Enabled: Disable Authenticated Proxy usage' | | Win OS-16 - Registry Policy | Ensure 'Turn off location' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Restrict Remote Desktop Services users to a single Remote Desktop Services session' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow COM port redirection' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow LPT port redirection' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow supported Plug and Play device redirection' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Set time limit for active but idle Remote Desktop Services sessions' is set to 'Enabled: 15 minutes or less' | | Win OS-16 - Registry Policy | Ensure 'Set time limit for disconnected sessions' is set to 'Enabled: 1 minute' | | Win OS-16 - Registry Policy | Ensure 'Allow Cloud Search' is set to 'Enabled: Disable Cloud Search' | | Win OS-16 - Registry Policy | Ensure 'Join Microsoft MAPS' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off KMS Client Online AVS Validation' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow suggested apps in Windows Ink Workspace' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Watson events' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow remote server management through WinRM' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Prevent Internet Explorer security prompt for Windows Installer scripts' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Prohibit connection to non-domain networks when connected to domain authenticated network' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Allow Remote Shell Access' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Enable Windows NTP Server' is set to 'Disabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Restrict Unauthenticated RPC clients' is set to 'Enabled: Authenticated' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Turn On Virtualization Based Security: Select Platform Security Level' is set to 'Secure Boot and DMA Protection' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Turn On Virtualization Based Security' is set to 'Enabled' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Turn On Virtualization Based Security: Require UEFI Memory Attributes Table' is set to 'True (checked)' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Turn On Virtualization Based Security: Virtualization Based Protection of Code Integrity' is set to 'Enabled with UEFI lock' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Turn On Virtualization Based Security: Credential Guard Configuration' is set to 'Enabled with UEFI lock' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Audit Distribution Group Management' is set to 'Success and Failure' (DC only) | | Win OS-16 - Registry Policy | Ensure 'Audit Other Account Management Events' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Ensure 'Audit Computer Account Management' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Ensure 'Audit Security Group Management' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Ensure 'Audit Process Creation' is set to 'Success' | | Win OS-16 - Registry Policy | Ensure 'Audit Audit Policy Change' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Ensure 'Audit Security System Extension' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Ensure 'Audit System Integrity' is set to 'Success and Failure' | | Win OS-16 - Registry Policy | Configure 'Network access: Named Pipes that can be accessed anonymously' (DC only) | | Win OS-16 - Registry Policy | Ensure 'Accounts: Administrator account status' is set to 'Disabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Accounts: Block Microsoft accounts' is set to 'Users can't add or log on with Microsoft accounts' | | Win OS-16 - Registry Policy | Configure 'Accounts: Rename administrator account' | | Win OS-16 - Registry Policy | Configure 'Accounts: Rename guest account' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Digitally encrypt or sign secure channel data (always)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Digitally encrypt secure channel data (when possible)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Digitally sign secure channel data (when possible)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Disable machine account password changes' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Maximum machine account password age' is set to '30 or fewer days, but not 0' | | Win OS-16 - Registry Policy | Ensure 'Domain member: Require strong (Windows 2000 or later) session key' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Machine inactivity limit' is set to '900 or fewer second(s), but not 0' | | Win OS-16 - Registry Policy | Configure 'Interactive logon: Message text for users attempting to log on' | | Win OS-16 - Registry Policy | Configure 'Interactive logon: Message title for users attempting to log on' | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Prompt user to change password before expiration' is set to 'between 5 and 14 days' | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Require Domain Controller Authentication to unlock workstation' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Smart card removal behavior' is set to 'Lock Workstation' or higher | | Win OS-16 - Registry Policy | Ensure 'Microsoft network server: Server SPN target name validation level' is set to 'Accept if provided by client' or higher (MS only) | | Win OS-16 - Registry Policy | Ensure 'Network access: Allow anonymous SID/Name translation' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled' | | Win OS-16 - Registry Policy | Configure 'Network access: Named Pipes that can be accessed anonymously' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Number of previous logons to cache (in case domain controller is not available)' is set to '4 or fewer logon(s)' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Inbound connections' is set to 'Block (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Logging: Name' is set to '%SYSTEMROOT%\System32\logfiles\firewall\domainfw.log' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Logging: Size limit (KB)' is set to '16,384 KB or greater' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Logging: Log dropped packets' is set to 'Yes' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Logging: Log successful connections' is set to 'Yes' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Inbound connections' is set to 'Block (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Logging: Name' is set to '%SYSTEMROOT%\System32\logfiles\firewall\privatefw.log' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Logging: Size limit (KB)' is set to '16,384 KB or greater' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Logging: Log dropped packets' is set to 'Yes' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Logging: Log successful connections' is set to 'Yes' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Inbound connections' is set to 'Block (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Settings: Apply local firewall rules' is set to 'No' |**Added** the following 167 new OS hardening policies for Windows Server 2016 server hosted in an AWS cloud account
| Category | Policy Title | |-----------------------------|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------| | Win OS-16 - Registry Policy | Ensure 'Include command line in process creation events' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Disallow Digest authentication' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off app notifications on the lock screen' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off downloading of print drivers over HTTP' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Solicited Remote Assistance' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Offer Remote Assistance' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Autoplay' is set to 'Enabled: All drives' | | Win OS-16 - Registry Policy | Ensure 'Disallow Autoplay for non-volume devices' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Enumerate administrator accounts on elevation' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Do not display the password reveal button' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-16 - Registry Policy | Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-16 - Registry Policy | Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater' | | Win OS-16 - Registry Policy | Ensure 'Turn off Data Execution Prevention for Explorer' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off heap termination on corruption' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off shell protocol protected mode' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Require secure RPC communication' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Prevent downloading of enclosures' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Set client connection encryption level' is set to 'Enabled: High Level' | | Win OS-16 - Registry Policy | Ensure 'Sign-in last interactive user automatically after a system-initiated restart' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Turn on convenience PIN sign-in' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Do not allow passwords to be saved' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow Basic authentication' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow user control over installs' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Configure Windows Defender SmartScreen' is set to 'Enabled: Warn and prevent bypass' | | Win OS-16 - Registry Policy | Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Disallow WinRM from storing RunAs credentials' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network client: Digitally sign communications (always)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Do not display last user name' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network server: Digitally sign communications (if client agrees)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network client: Digitally sign communications (if server agrees)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Outbound connections' is set to 'Allow (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Firewall state' is set to 'On (recommended)' | | Win OS-16 - Registry Policy | Ensure 'Devices: Allowed to format and eject removable media' is set to 'Administrators' | | Win OS-16 - Registry Policy | Ensure 'Accounts: Limit local account use of blank passwords to console logon only' is set to 'Enabled' | | Win OS-16 - Registry Policy | Configure 'Network access: Remotely accessible registry paths and sub-paths' | | Win OS-16 - Registry Policy | Ensure 'Interactive logon: Do not require CTRL+ALT+DEL' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves' | | Win OS-16 - Registry Policy | Configure 'Network access: Remotely accessible registry paths' | | Win OS-16 - Registry Policy | Ensure 'Network security: Configure encryption types allowed for Kerberos' is set to 'AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types' | | Win OS-16 - Registry Policy | Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv2 session security, Require 128-bit encryption' | | Win OS-16 - Registry Policy | Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM & NTLM' | | Win OS-16 - Registry Policy | Ensure 'Shutdown: Allow system to be shut down without having to log on' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv2 session security, Require 128-bit encryption' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Admin Approval Mode for the Built-in Administrator account' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'System objects: Strengthen default permissions of internal system objects (e.g. Symbolic Links)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode' is set to 'Prompt for consent on the secure desktop' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Detect application installations and prompt for elevation' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Behavior of the elevation prompt for standard users' is set to 'Automatically deny elevation requests' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Run all administrators in Admin Approval Mode' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Only elevate UIAccess applications that are installed in secure locations' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Virtualize file and registry write failures to per-user locations' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'User Account Control: Switch to the secure desktop when prompting for elevation' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Outbound connections' is set to 'Allow (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Settings: Display a notification' is set to 'No' | | Win OS-16 - Registry Policy | Ensure 'Always install with elevated privileges' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Settings: Apply local connection security rules' is set to 'No' | | Win OS-16 - Registry Policy | Ensure 'Enable insecure guest logons' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Prohibit use of Internet Connection Sharing on your DNS domain network' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Internet Connection Wizard if URL connection is referring to Microsoft.com' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Block user from showing account details on sign-in' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Enable Windows NTP Client' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Turn off Microsoft consumer experiences' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow Telemetry' is set to 'Enabled: 0 - Security [Enterprise Only]' or 'Enabled: 1 - Basic' | | Win OS-16 - Registry Policy | Ensure 'Turn off multicast name resolution' is set to 'Enabled' (MS Only) | | Win OS-16 - Registry Policy | Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Prevent enabling lock screen camera' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Allow input personalization' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Continue experiences on this device' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Do not show feedback notifications' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Shut down the system' is set to 'Administrators' | | Win OS-16 - Registry Policy | Ensure 'Enable RPC Endpoint Mapper Client Authentication' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Prohibit installation and configuration of Network Bridge on your DNS domain network' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Boot-Start Driver Initialization Policy' is set to 'Enabled: Good, unknown and bad but critical' | | Win OS-16 - Registry Policy | Ensure 'Set the default behavior for AutoRun' is set to 'Enabled: Do not execute any autorun commands' | | Win OS-16 - Registry Policy | Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater' | | Win OS-16 - Registry Policy | Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Always prompt for password upon connection' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not delete temp folders upon exit' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Do not use temporary folders per session' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow indexing of encrypted files' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Allow unencrypted traffic' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network client: Send unencrypted password to third-party SMB servers' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled' (MS only) | | Win OS-16 - Registry Policy | Ensure 'Microsoft network server: Amount of idle time required before suspending session' is set to '15 or fewer minute(s), but not 0' | | Win OS-16 - Registry Policy | Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Domain: Settings: Display a notification' is set to 'No' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Firewall state' is set to 'On (recommended)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Private: Outbound connections' is set to 'Allow (default)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Firewall state' is set to 'On (recommended)' | | Win OS-16 - Registry Policy | Ensure 'Windows Firewall: Public: Settings: Apply local firewall rules' is set to 'No' | | Win OS-16 - Registry Policy | Ensure 'Prevent enabling lock screen slide show' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Minimize the number of simultaneous connections to the Internet or a Windows Domain' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Do not display network selection UI' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Devices: Prevent users from installing printer drivers' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network server: Disconnect clients when logon hours expire' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'System objects: Require case insensitivity for non-Windows subsystems' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Microsoft network server: Digitally sign communications (always)' is set to 'Enabled' | | Win OS-16 - Registry Policy | Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None' | | Win OS-16 - Registry Policy | Ensure 'Allow Microsoft accounts to be optional' is set to 'Enabled' | | Win OS-16 - Security Policy | Ensure 'Allow log on through Remote Desktop Services' is set to 'Administrators' (DC only) | | Win OS-16 - Security Policy | Ensure 'Replace a process level token' is set to 'LOCAL SERVICE, NETWORK SERVICE' | | Win OS-16 - Security Policy | Ensure 'Enable computer and user accounts to be trusted for delegation' is set to 'Administrators' (DC only) | | Win OS-16 - Security Policy | Ensure 'Create symbolic links' is set to 'Administrators' (DC only) | | Win OS-16 - Security Policy | Ensure 'Manage auditing and security log' is set to 'Administrators' and (when Exchange is running in the environment) 'Exchange Servers' (DC only) | | Win OS-16 - Security Policy | Ensure 'Modify an object label' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Enforce password history' is set to '24 or more password(s)' | | Win OS-16 - Security Policy | Ensure 'Maximum password age' is set to '60 or fewer days, but not 0' | | Win OS-16 - Security Policy | Ensure 'Minimum password age' is set to '1 or more day(s)' | | Win OS-16 - Security Policy | Ensure 'Minimum password length' is set to '14 or more character(s)' | | Win OS-16 - Security Policy | Ensure 'Password must meet complexity requirements' is set to 'Enabled' | | Win OS-16 - Security Policy | Ensure 'Store passwords using reversible encryption' is set to 'Disabled' | | Win OS-16 - Security Policy | Ensure 'Act as part of the operating system' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Access Credential Manager as a trusted caller' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Change the system time' is set to 'Administrators, LOCAL SERVICE' | | Win OS-16 - Security Policy | Ensure 'Back up files and directories' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Create a pagefile' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Change the time zone' is set to 'Administrators, LOCAL SERVICE' | | Win OS-16 - Security Policy | Ensure 'Create global objects' is set to 'Administrators, LOCAL SERVICE, NETWORK SERVICE, SERVICE' | | Win OS-16 - Security Policy | Ensure 'Create a token object' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Deny log on as a batch job' to include 'Guests' | | Win OS-16 - Security Policy | Ensure 'Create permanent shared objects' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Deny log on locally' to include 'Guests' | | Win OS-16 - Security Policy | Ensure 'Deny log on as a service' to include 'Guests' | | Win OS-16 - Security Policy | Ensure 'Load and unload device drivers' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Generate security audits' is set to 'LOCAL SERVICE, NETWORK SERVICE' | | Win OS-16 - Security Policy | Ensure 'Perform volume maintenance tasks' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Lock pages in memory' is set to 'No One' | | Win OS-16 - Security Policy | Ensure 'Restore files and directories' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Profile single process' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Take ownership of files or other objects' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Modify firmware environment values' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Access this computer from the network' is set to 'Administrators, Authenticated Users, ENTERPRISE DOMAIN CONTROLLERS' (DC only) | | Win OS-16 - Security Policy | Ensure 'Force shutdown from a remote system' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Profile system performance' is set to 'Administrators, NT SERVICE\WdiServiceHost' | | Win OS-16 - Security Policy | Ensure 'Deny log on through Remote Desktop Services' is set to 'Guests' (DC only) | | Win OS-16 - Security Policy | Ensure 'Increase scheduling priority' is set to 'Administrators' | | Win OS-16 - Security Policy | Ensure 'Deny access to this computer from the network' is set to 'Guests' (DC only) | | Win OS-16 - Security Policy | Ensure 'Accounts: Guest account status' is set to 'Disabled' (MS only) | | Win OS-16 - Security Policy | Ensure 'Allow log on locally' is set to 'Administrators' | | Win OS-16 - Audit Policy | Ensure 'Audit Account Lockout' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Special Logon' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Authorization Policy Change' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit Removable Storage' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Group Membership' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Logoff' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit User Account Management' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Other System Events' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Logon' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit IPsec Driver' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Security State Change' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit Application Group Management' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit Other Object Access Events' is set to 'Success and Failure' | | Win OS-16 - Audit Policy | Ensure 'Audit PNP Activity' is set to 'Success' | | Win OS-16 - Audit Policy | Ensure 'Audit Authentication Policy Change' is set to 'Success' |**Added** following 44 AWS Red Hat Enterprise Linux (RHEL) VM Baseline policies
| **Category** | **Policy name** | |---------------------------------------------------|------------------------------------------------------------------------| | RHEL 7 - Initial Setup | Ensure bootloader password is set | | RHEL 7 - Initial Setup | Ensure authentication required for single user mode | | RHEL 7 - Initial Setup | Ensure separate partition exists for /tmp | | RHEL 7 - Initial Setup | Ensure separate partition exists for /var | | RHEL 7 - Initial Setup | Ensure separate partition exists for /var/tmp | | RHEL 7 - Initial Setup | Ensure separate partition exists for /var/log | | RHEL 7 - Initial Setup | Ensure separate partition exists for /var/log/audit | | RHEL 7 - Initial Setup | Ensure separate partition exists for /home | | RHEL 7 - Initial Setup | Ensure mounting of FAT filesystems is disabled | | RHEL 7 - Initial Setup | Ensure GDM login banner is configured | | RHEL 7 - Initial Setup | Ensure message of the day is configured properly | | RHEL 7 - Services | Ensure mail transfer agent is configured for local-only mode | | RHEL 7 - Network Configuration | Ensure /etc/hosts.allow is configured | | RHEL 7 - Network Configuration | Ensure /etc/hosts.deny is configured | | RHEL 7 - Network Configuration | Ensure permissions on /etc/hosts.allow are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure access to the su command is restricted | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/crontab are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/cron.hourly are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/cron.daily are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/cron.weekly are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/cron.monthly are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/cron.d are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure permissions on /etc/ssh/sshd_config are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure password creation requirements are configured | | RHEL 7 - Access, Authentication and Authorization | Ensure system accounts are non-login | | RHEL 7 - Access, Authentication and Authorization | Ensure inactive password lock is 30 days or less | | RHEL 7 - System Maintenance | Ensure permissions on /etc/passwd are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/shadow are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/group are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/gshadow are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/passwd- are configured | | RHEL 7 - System Maintenance | Ensure password fields are not empty | | RHEL 7 - System Maintenance | Ensure root PATH Integrity | | RHEL 7 - System Maintenance | Ensure all users' home directories exist | | RHEL 7 - System Maintenance | Ensure users' home directories permissions are 750 or more restrictive | | RHEL 7 - System Maintenance | Ensure users own their home directories | | RHEL 7 - System Maintenance | Ensure users' dot files are not group or world writable | | RHEL 7 - System Maintenance | Ensure users' .netrc Files are not group or world accessible | | RHEL 7 - System Maintenance | Ensure no users have .rhosts files | | RHEL 7 - System Maintenance | Ensure all groups in /etc/passwd exist in /etc/group | | RHEL 7 - System Maintenance | Ensure no duplicate UIDs exist | | RHEL 7 - System Maintenance | Ensure no duplicate GIDs exist | | RHEL 7 - System Maintenance | Ensure no duplicate user names exist | | RHEL 7 - System Maintenance | Ensure no duplicate group names exist |**Added** the following 2 new security policies for AWS cloud account
| **Category** | **Policy name** | |-----------------------------|------------------------------------------------------------------------------------------------------------------------------------------------------| | AWS - Compute | Ensure that EC2 instances provisioned in your AWS account are not associated with security groups that have their name prefixed with 'launch-wizard' | | AWS - Storage and Databases | Ensure that AWS S3 buckets use Object Lock for data protection and/or regulatory compliance |**Updated** following 3 policies for M365 to automatically get data from Microsoft 365 using automation account (PS).
| **Category** | **Policy name** | |--------------|-----------------------------------------------------------------| | M365 - Data | Enable audit data recording | | M365 - Data | Ensure Advanced Threat Protection safe attach policy is Enabled | | M365 - Data | Ensure Advanced Threat Protection safe links policy is Enabled |**Updated** following 10 AWS policies as Manual as AWS config API does not support these as of now
| **Category** | **Policy name** | |----------------------------------|-----------------------------------------------------------------------------------------------------------------------------------------| | AWS - Compute | Ensure all AWS EC2 instances are launched from approved AMIs | | AWS - Compute | Ensure no backend EC2 instances are running in public subnets | | AWS - Compute | Ensure every EC2 instance is launched inside an Auto Scaling Group (ASG) in order to follow AWS reliability and security best practices | | AWS - Compute | Ensure that there are no AWS EC2 instances that have scheduled events | | AWS - Compute | Ensure that the security group(s) associated with an EC2 instance does not have an excessive number of rules defined | | AWS - Compute | Ensure Termination Protection feature is enabled for EC2 instances that are not part of ASGs | | AWS - Compute | "Ensure no EC2 security group allows inbound traffic from RFC-1918 CIDRs in order to follow AWS security best practices" | | AWS - Data In Transit Encryption | Ensure EBS volumes are encrypted with KMS CMKs in order to have full control over data encryption and decryption | | AWS - Audit and Logging | Ensure that Object level write event log is enabled for S3 bucket | | AWS - Audit and Logging | Ensure that Object level read event log is enabled for S3 bucket |Added following 21 AWS Elastic Kubernetes Service (EKS) related policies
| **Category Name** | **Policy Title** | |-------------------------------------------------------------|---------------------------------------------------------------------------------------------| | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet service file has permissions of 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet service file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the proxy kubeconfig file permissions are set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the proxy kubeconfig file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet.conf file permissions are set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet.conf file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the client certificate authorities file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet configuration file has permissions set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet configuration file ownership is set to root:root | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --anonymous-auth argument is set to false | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --authorization-mode argument is not set to AlwaysAllow | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --client-ca-file argument is set as appropriate | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --read-only-port argument is set to 0 | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --streaming-connection-idle-timeout argument is not set to 0 | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --protect-kernel-defaults argument is set to true | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --make-iptables-util-chains argument is set to true | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --hostname-override argument is not set | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --tls-cert-file and --tls-private-key-file arguments are set as appropriate | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --rotate-certificates argument is not set to false | | Kubernetes - Worker Nodes - Kubelet | Ensure that the RotateKubeletServerCertificate argument is set to true | | Kubernetes - Worker Nodes - Kubelet | Ensure that the Kubelet only makes use of Strong Cryptographic Ciphers |Added following 25 manual policies for Azure
| **Category** | **Policy name** | |---------------------------------|----------------------------------------------------------------------------------------------------------------------------------| | Azure - Kubernetes & Containers | Ensure that credentials of service principal used for Container Registry are stored in Key Vault | | Azure - Kubernetes & Containers | Ensure that Container Registry has latest/patched image(s) all the time | | Azure - Kubernetes & Containers | Ensure that Activity logs for Data Container Registry are reviewed periodically | | Azure - Kubernetes & Containers | Ensure that only signed images are pushed to Container Registry | | Azure - Kubernetes & Containers | Ensure that a service principal is used to access container images in Container Registry | | Azure - Kubernetes & Containers | Ensure that all users/identities are granted minimum required permissions using Role Based Access Control (RBAC) | | Azure - Kubernetes & Containers | Ensure that management ports are not kept open on Kubernetes nodes unless required | | Azure - Kubernetes & Containers | Ensure that cluster admin level access is not directly or indirectly granted to developers | | Azure - Kubernetes & Containers | Ensure that container images (including nested images) deployed in Kubernetes are from a trustworthy source | | Azure - Kubernetes & Containers | Ensure that default cluster namespace is not used to deploy applications | | Azure - Kubernetes & Containers | Ensure that all Kubernetes Service secrets are stored in Key Vault | | Azure - Kubernetes & Containers | Ensure that all the Kubernetes cluster nodes have all the required OS patches installed | | Azure - Kubernetes & Containers | Ensure that Pod Identity is used for accessing other AAD(Azure Active Directory)-protected resources from the Kubernetes Service | | Azure - Kubernetes & Containers | Ensure that issues/recommendations provided by kube advisor are reviewed periodically | | Azure - Kubernetes & Containers | Ensure that data transit inside/across Kubernetes are using encrypted channel | | Azure - Kubernetes & Containers | Ensure that all users/identities are granted minimum required permissions using Role Based Access Control (RBAC) | | Azure - Storage and Databases | Ensure that secrets and keys must not be in plain text in notebooks and jobs | | Azure - Storage and Databases | Ensure that use Azure Key Vault backed secret scope to hold secrets | | Azure - Storage and Databases | Ensure that all users/identities must be granted minimum required permissions using Role Based Access Control (RBAC) | | Azure - Storage and Databases | Ensure that Minimize the number of workspace admins | | Azure - Storage and Databases | Ensure that All users must be granted minimum required permissions on clusters | | Azure - Storage and Databases | Ensure that the parameterized SQL queries used to access the database | | Azure - Storage and Databases | Ensure that CosmosDb Account keys are rotated periodically | | Azure - Storage and Databases | Ensure that resource tokens are generated with least privileges and expiry needed by clients | | Azure - Storage and Databases | Do not send resource token with read write (RW) permission to untrusted clients |Updated following 16 policies for M365 to automatically get data from Microsoft 365 security APIs.
| **Category Name** | **Policy Name** | |-------------------|------------------------------------------------------------------------------| | M365 - Device | Create a Microsoft Intune Compliance Policy for iOS | | M365 - Device | Create a Microsoft Intune Compliance Policy for Android | | M365 - Device | Create a Microsoft Intune Compliance Policy for Android for Work | | M365 - Device | Create a Microsoft Intune Compliance Policy for Windows | | M365 - Device | Create a Microsoft Intune Compliance Policy for macOS | | M365 - Device | Create a Microsoft Intune App Protection Policy for iOS | | M365 - Device | Create a Microsoft Intune App Protection Policy for Android | | M365 - Device | Create a Microsoft Intune Windows Information Protection Policy | | M365 - Device | Create a Microsoft Intune Configuration Profile for iOS | | M365 - Device | Create a Microsoft Intune Configuration Profile for Android | | M365 - Device | Create a Microsoft Intune Configuration Profile for Android for Work | | M365 - Device | Create a Microsoft Intune Configuration Profile for Windows | | M365 - Device | Create a Microsoft Intune Configuration Profile for macOS | | M365 - Device | Require mobile devices to manage email profile | | M365 - Device | Ensure that users cannot connect from devices that are jail broken or rooted | | M365 - Device | Enable Enhanced Jailbreak Detection in Microsoft Intune |Added the following 33 AWS security policies for Auto remediation
| **Policy Title** | |-----------------------------------------------------------------------------------------------------------------------------------------------| | Ensure AWS Neptune clusters have a sufficient backup retention period set for compliance purposes | | Ensure IAM Database Authentication feature is enabled for Amazon Neptune clusters | | Ensure Amazon Neptune instances have Auto Minor Version Upgrade feature enabled | | Ensure Log Exports feature is enabled for RDS Aurora MySQL Serverless Cluster | | Ensure Log Exports feature is enabled for RDS MySQL Instance | | Ensure Log Exports feature is enabled for RDS Mariadb Instance | | Ensure Log Exports feature is enabled for Aurora cluster | | Ensure Log Exports feature is enabled for Oracle instances | | Ensure Auto Minor Version Upgrade feature is Enabled for RDS MySQL Instances | | Ensure backup retention policy is set for RDS MySQL Instances | | Ensure that Copy Tags to Snapshots feature is enabled for RDS MySQL Instances | | Ensure Deletion Protection feature is enabled for RDS MySQL Instances | | Ensure Performance Insights feature is enabled for RDS MySQL Instances | | Ensure that public access is not given to RDS MySQL Instance | | Ensure Multi-AZ feature is Enabled for RDS MySQL Instance | | Ensure that sufficient backup retention period is applied to RDS MySQL Instances | | Ensure that detailed monitoring is enabled for the AWS EC2 instances that you need to monitor closely | | Ensure Termination Protection feature is enabled for EC2 instances that are not part of ASGs | | Ensure Amazon Auto Scaling Groups are utilizing cooldown periods | | Ensure Global resources are included into Amazon Config service configuration | | Ensure Amazon DynamoDB tables have continuous backups enabled | | Ensure that Server-Side Encryption is enabled for Amazon SQS queues | | Ensure that Termination Protection feature is enabled for AWS CloudFormation stacks | | Ensure that CloudTrail trail have logging enabled | | Ensure that Amazon S3 buckets use Transfer Acceleration feature for faster data transfers | | Ensure that S3 buckets are not publicly accessible | | Ensure IAM Database Authentication feature is enabled for RDS Postgre Instances | | Ensure IAM Database Authentication feature is enabled for RDS Aurora Cluster | | Ensure IAM Database Authentication feature is enabled for RDS MySQL Instances | | Ensure that Amazon RDS database snapshots are not accessible to all AWS accounts | | Ensure Amazon Kinesis streams enforce Server-Side Encryption (SSE) | | Ensure to enable FIPS standards on the server side for RDS MySQL Instance --not applicable for rds instance using default parameter group | | Ensure that latest block encryption algorithms is used for RDS MySQL Instance --not applicable for rds instance using default parameter group |Added following 73 Azure Kubernetes Service (AKS) related policies
| **Category** | **Policy Title** | | --- | --- | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the API server pod specification file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the API server pod specification file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the controller manager pod specification file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the controller manager pod specification file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the scheduler pod specification file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the scheduler pod specification file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the etcd pod specification file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the etcd pod specification file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the etcd data directory permissions are set to 700 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the etcd data directory ownership is set to etcd:etcd | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the admin.conf file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the admin.conf file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the scheduler.conf file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the scheduler.conf file ownership is set to root:root | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the controller-manager.conf file permissions are set to 644 or more restrictive | | Kubernetes - Control Plane Components - Master Node Configuration Files | Ensure that the controller-manager.conf file ownership is set to root:root | | Kubernetes - Control Plane Components - API Server | Ensure that the --basic-auth-file argument is not set | | Kubernetes - Control Plane Components - API Server | Ensure that the --token-auth-file argument is not set | | Kubernetes - Control Plane Components - API Server | Ensure that the --kubelet-https argument is set to true | | Kubernetes - Control Plane Components - API Server | Ensure that the --kubelet-client-certificate and --kubelet-client-key arguments are set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --kubelet-certificate-authority argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --authorization-mode argument is not set to AlwaysAllow | | Kubernetes - Control Plane Components - API Server | Ensure that the --authorization-mode argument includes Node | | Kubernetes - Control Plane Components - API Server | Ensure that the --authorization-mode argument includes RBAC | | Kubernetes - Control Plane Components - API Server | Ensure that the admission control plugin AlwaysAdmit is not set | | Kubernetes - Control Plane Components - API Server | Ensure that the admission control plugin ServiceAccount is set | | Kubernetes - Control Plane Components - API Server | Ensure that the admission control plugin NamespaceLifecycle is set | | Kubernetes - Control Plane Components - API Server | Ensure that the admission control plugin PodSecurityPolicy is set | | Kubernetes - Control Plane Components - API Server | Ensure that the admission control plugin NodeRestriction is set | | Kubernetes - Control Plane Components - API Server | Ensure that the --insecure-bind-address argument is not set | | Kubernetes - Control Plane Components - API Server | Ensure that the --insecure-port argument is set to 0 | | Kubernetes - Control Plane Components - API Server | Ensure that the --secure-port argument is not set to 0 | | Kubernetes - Control Plane Components - API Server | Ensure that the --profiling argument is set to false | | Kubernetes - Control Plane Components - API Server | Ensure that the --request-timeout argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --service-account-lookup argument is set to true | | Kubernetes - Control Plane Components - API Server | Ensure that the --service-account-key-file argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --etcd-certfile and --etcd-keyfile arguments are set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --tls-cert-file and --tls-private-key-file arguments are set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --client-ca-file argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --etcd-cafile argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --encryption-provider-config argument is set as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --audit-log-path argument is set | | Kubernetes - Control Plane Components - API Server | Ensure that the --audit-log-maxage argument is set to 30 or as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --audit-log-maxbackup argument is set to 10 or as appropriate | | Kubernetes - Control Plane Components - API Server | Ensure that the --audit-log-maxsize argument is set to 100 or as appropriate | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --terminated-pod-gc-threshold argument is set as appropriate | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --profiling argument is set to false | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --use-service-account-credentials argument is set to true | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --service-account-private-key-file argument is set as appropriate | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --root-ca-file argument is set as appropriate | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the RotateKubeletServerCertificate argument is set to true | | Kubernetes - Control Plane Components - Controller Manager | Ensure that the --bind-address argument is set to 127.0.0.1 | | Kubernetes - Control Plane Components - Scheduler | Ensure that the --profiling argument is set to false | | Kubernetes - Control Plane Components - Scheduler | Ensure that the --bind-address argument is set to 127.0.0.1 | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet service file has permissions of 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet service file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the proxy kubeconfig file permissions are set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the proxy kubeconfig file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet.conf file permissions are set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet.conf file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the client certificate authorities file ownership is set to root:root | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet configuration file has permissions set to 644 or more restrictive | | Kubernetes - Worker Nodes - Worker Node Configuration Files | Ensure that the kubelet configuration file ownership is set to root:root | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --anonymous-auth argument is set to false | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --authorization-mode argument is not set to AlwaysAllow | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --client-ca-file argument is set as appropriate | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --read-only-port argument is set to 0 | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --streaming-connection-idle-timeout argument is not set to 0 | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --protect-kernel-defaults argument is set to true | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --make-iptables-util-chains argument is set to true | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --tls-cert-file and --tls-private-key-file arguments are set as appropriate | | Kubernetes - Worker Nodes - Kubelet | Ensure that the --rotate-certificates argument is not set to false | | Kubernetes - Worker Nodes - Kubelet | Ensure that the RotateKubeletServerCertificate argument is set to true |Added following 14 AWS Red Hat Enterprise Linux (RHEL) VM Baseline policies
| **Category** | **Policy Title** | | --- | --- | | RHEL 7 - Initial Setup | Ensure local login warning banner is configured properly | | RHEL 7 - Initial Setup | Ensure remote login warning banner is configured properly | | RHEL 7 - Initial Setup | Ensure permissions on /etc/motd are configured | | RHEL 7 - Initial Setup | Ensure permissions on /etc/issue.net are configured | | RHEL 7 - Network Configuration | Ensure IPv6 router advertisements are not accepted | | RHEL 7 - Network Configuration | Ensure IPv6 redirects are not accepted | | RHEL 7 - Network Configuration | Ensure IPv6 is disabled | | RHEL 7 - Network Configuration | Ensure permissions on /etc/hosts.deny are 644 | | RHEL 7 - Network Configuration | Ensure DCCP is disabled | | RHEL 7 - Network Configuration | Ensure SCTP is disabled | | RHEL 7 - Network Configuration | Ensure RDS is disabled | | RHEL 7 - Network Configuration | Ensure TIPC is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure password expiration is 90 days or less | | RHEL 7 - Initial Setup | Ensure XD/NX support is enabled |Added following 6 manual policies for Azure
| **Category** | **Policy Title** | | --- | --- | | Azure - Storage and Databases | Ensure that shared access signature tokens are allowed only over https | | Azure - Storage and Databases | Ensure that shared access signature tokens expire within an hour | | Azure - Storage and Databases | Ensure Storage logging is enabled for Queue service for read, write, and delete requests | | Azure - Storage and Databases | Ensure that storage account access keys are periodically regenerated | | Azure - Compute (IaaS) | Ensure that only approved extensions are installed | | Azure - Identity and Access | Ensure that multi-factor authentication is enabled for all privileged users |Added following 3 manual policies for AWS
| **Category** | **Policy Title** | | --- | --- | | AWS - Identity and Access Management | Ensure security questions are registered in the AWS account | | AWS - Identity and Access Management | Maintain current contact details | | AWS - Identity and Access Management | Ensure security contact information is registered |Added following 16 manual policies for M365
| **Category** | **Policy Title** | | --- | --- | | M365 - Account / Authentication | Ensure modern authentication for Skype for Business Online is enabled | | M365 - Identity | Ensure that password protection is enabled for Active Directory in hybrid environments | | M365 - Auditing | Ensure mailbox auditing for all users is Enabled | | M365 - Auditing | Ensure the self-service password reset activity report is reviewed at least weekly | | M365 - Auditing | Ensure mail forwarding rules are reviewed at least weekly | | M365 - Auditing | Ensure non-global administrator role group assignments are reviewed at least weekly | | M365 - Auditing | Ensure the report of users who have had their email privileges restricted due to spamming is reviewed | | M365 - Auditing | Ensure Guest Users are reviewed at least biweekly | | M365 - Device | Ensure mobile device management polices are set to require advanced security configurations to protect from basic internet attacks | | M365 - Device | Ensure that devices connecting have AV and a local firewall enabled | | M365 - Data | Ensure external domains are not allowed in Skype or Teams | | M365 - Data | Ensure external file sharing in Teams is enabled for only approved cloud storage services | | M365 - Auditing | Ensure the Application Usage report is reviewed at least weekly | | M365 - Identity | Enabled Identity Protection to identify anomalous logon behavior | | M365 - Data | Ensure DLP policies are enabled for Microsoft Teams | | M365 - Identity | Use Just In Time privileged access to Office 365 roles | | M365 - Identity | Ensure the Azure AD 'Risky sign-ins' report is reviewed at least weekly |Updated following 42 policies for M365 as manual as data from secure score API (Microsoft Office API) is deprecated
| **Category** | **Policy Title** | | --- | --- | | M365 - Apps | Enable Microsoft 365 Cloud App Security | | M365 - Apps | Discover risky and non-compliant Shadow IT applications used in your organization | | M365 - Apps | Review permissions & block risky OAuth applications connected to your corporate environment | | M365 - Apps | Ensure that AD Application keys are rotated before they expires | | M365 - Data | Enable audit data recording | | M365 - Data | Store user documents in OneDrive for Business | | M365 - Data | Review audit data for illicit activity detection and security breach | | M365 - Data | Ensure mail transport rules do not forward email to external domains | | M365 - Data | Ensure mailbox access by non-owners report is reviewed bi-weekly | | M365 - Data | Ensure malware detections report is reviewed weekly | | M365 - Data | Ensure expiration time for external sharing links is set | | M365 - Data | Enable versioning on all SharePoint online document libraries | | M365 - Data | Review list of external users you have invited to documents monthly | | M365 - Data | Do not allow mailbox delegation | | M365 - Data | Allow anonymous guest sharing links for sites and docs | | M365 - Data | Ensure Advanced Threat Protection safe attach policy is Enabled | | M365 - Data | Ensure Advanced Threat Protection safe links policy is Enabled | | M365 - Device | Require mobile devices to manage email profile | | M365 - Device | Ensure that users cannot connect from devices that are jail broken or rooted | | M365 - Device | Enable mobile device management services | | M365 - Device | Require mobile devices to block access and report policy violations | | M365 - Device | Enable Microsoft Intune Mobile Device Management | | M365 - Device | Create a Microsoft Intune Compliance Policy for iOS | | M365 - Device | Create a Microsoft Intune Compliance Policy for Android | | M365 - Device | Create a Microsoft Intune Compliance Policy for Android for Work | | M365 - Device | Create a Microsoft Intune Compliance Policy for Windows | | M365 - Device | Create a Microsoft Intune Compliance Policy for macOS | | M365 - Device | Create a Microsoft Intune App Protection Policy for iOS | | M365 - Device | Create a Microsoft Intune App Protection Policy for Android | | M365 - Device | Create a Microsoft Intune Windows Information Protection Policy | | M365 - Device | Create a Microsoft Intune Configuration Profile for iOS | | M365 - Device | Create a Microsoft Intune Configuration Profile for Android | | M365 - Device | Create a Microsoft Intune Configuration Profile for Android for Work | | M365 - Device | Create a Microsoft Intune Configuration Profile for Windows | | M365 - Device | Create a Microsoft Intune Configuration Profile for macOS | | M365 - Device | Mark devices with no Microsoft Intune Compliance Policy assigned as Non Compliant | | M365 - Device | Enable Enhanced Jailbreak Detection in Microsoft Intune | | M365 - Device | Enable Windows Defender ATP integration into Microsoft Intune | | M365 - Identity | User alternate contact info is completed for all users | | M365 - Identity | Ensure multifactor authentication is enabled for all users in all roles | | M365 - Identity | Ensure that Service Principal Certificate are renewed before it expires | | M365 - Identity | Ensure the Azure AD 'Risky sign-ins' report is reviewed at least weekly |Added following 3 Azure account related policies
| **Category** | **Policy Title** | |-------------------------|--------------------------------------------------------------------------------------------------| | Azure - Security Center | Ensure that Kubernetes Services should be upgraded to a non-vulnerable Kubernetes version in ASC | | Azure - Security Center | Ensure that Vulnerabilities in container security configurations should be remediated in ASC | | Azure - Compute (IaaS) | Ensure that Virtual Machine's are used managed disks |Added following 38 AWS RHEL VM Baseline policies
| **Category** | **Policy Title** | |----------------------------------------------------|-------------------------------------------------------------| | RHEL 7 - Initial Setup | Ensure address space layout randomization (ASLR) is enabled | | RHEL 7 - Initial Setup | Ensure prelink is disabled | | RHEL 7 - Initial Setup | Ensure permissions on /etc/issue are configured | | RHEL 7 - Network Configuration | Ensure TCP SYN Cookies is enabled | | RHEL 7 - Network Configuration | Ensure TCP Wrappers is installed | | RHEL 7 - Network Configuration | Ensure iptables is installed | | RHEL 7 - Network Configuration | Ensure firewall rules exist for all open ports | | RHEL 7 - Access, Authentication and Authorization | Ensure default user shell timeout is 900 seconds or less | | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH X11 forwarding is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH MaxAuthTries is set to 4 or less | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH IgnoreRhosts is enabled | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH HostbasedAuthentication is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH root login is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH PermitEmptyPasswords is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH PermitUserEnvironment is disabled | | RHEL 7 - Access, Authentication and Authorization | Ensure only approved MAC algorithms are used | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH Idle Timeout Interval is configured | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH LoginGraceTime is set to one minute or less | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH access is limited | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH warning banner is configured | | RHEL 7 - Access, Authentication and Authorization | Ensure password reuse is limited | | RHEL 7 - Access, Authentication and Authorization | Ensure password hashing algorithm is SHA-512 | | RHEL 7 - Access, Authentication and Authorization | Ensure default group for the root account is GID 0 | | RHEL 7 - Access, Authentication and Authorization | Ensure minimum days between password changes is 7 or more | | RHEL 7 - Access, Authentication and Authorization | Ensure password expiration warning days is 7 or more | | RHEL 7 - Access, Authentication and Authorization | Ensure all users last password change date is in the past | | RHEL 7 - System Maintenance | Ensure permissions on /etc/shadow- are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/group- are configured | | RHEL 7 - System Maintenance | Ensure permissions on /etc/gshadow- are configured | | RHEL 7 - System Maintenance | Ensure no world writable files exist | | RHEL 7 - System Maintenance | Ensure no unowned files or directories exist | | RHEL 7 - System Maintenance | Ensure no ungrouped files or directories exist | | RHEL 7 - System Maintenance | Ensure no legacy "+" entries exist in /etc/passwd | | RHEL 7 - System Maintenance | Ensure no legacy "+" entries exist in /etc/shadow | | RHEL 7 - System Maintenance | Ensure no legacy "+" entries exist in /etc/group | | RHEL 7 - System Maintenance | Ensure root is the only UID 0 account | | RHEL 7 - System Maintenance | Ensure no users have .forward files | | RHEL 7 - System Maintenance | Ensure no users have .netrc files |Added following 66 AWS RHEL VM Baseline policies
| **Category** | **Policy Title** | |---------------------------------------------------|-------------------------------------------------------------------------| | RHEL 7 - Access, Authentication and Authorization | Ensure at/cron is restricted to authorized users | | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH Protocol is set to 2 | | | RHEL 7 - Access, Authentication and Authorization | Ensure SSH LogLevel is set to INFO | | | RHEL 7 - Access, Authentication and Authorization | Ensure default user shell timeout is 900 seconds or less | | | RHEL 7 - Initial Setup | Ensure updates, patches, and additional security software are installed | | | RHEL 7 - Initial Setup | Ensure nodev option set on /tmp partition | | | RHEL 7 - Initial Setup | Ensure nosuid option set on /tmp partition | | | RHEL 7 - Initial Setup | Ensure noexec option set on /tmp partition | | | RHEL 7 - Initial Setup | Ensure nodev option set on /dev/shm partition | | | RHEL 7 - Initial Setup | Ensure nosuid option set on /dev/shm partition | | | RHEL 7 - Initial Setup | Ensure noexec option set on /dev/shm partition | | | RHEL 7 - Initial Setup | Ensure mounting of cramfs filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of freevxfs filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of jffs2 filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of hfs filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of hfsplus filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of squashfs filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure mounting of udf filesystems is disabled | | | RHEL 7 - Initial Setup | Ensure gpgcheck is globally activated | | | RHEL 7 - Initial Setup | Ensure AIDE is installed | | | RHEL 7 - Initial Setup | Ensure filesystem integrity is regularly checked | | | RHEL 7 - Initial Setup | Ensure permissions on bootloader config are configured | | | RHEL 7 - Initial Setup | Ensure SELinux is installed | | | RHEL 7 - Initial Setup | Ensure SELinux is not disabled in bootloader configuration | | | RHEL 7 - Initial Setup | Ensure the SELinux state is enforcing | | | RHEL 7 - Initial Setup | Ensure SELinux policy is configured | | | RHEL 7 - Initial Setup | Ensure SETroubleshoot is not installed | | | RHEL 7 - Initial Setup | Ensure the MCS Translation Service (mcstrans) is not installed | | | RHEL 7 - Logging and Auditing | Ensure rsyslog or syslog-ng is installed | | | RHEL 7 - Logging and Auditing | Ensure permissions on all logfiles are configured | | | RHEL 7 - Logging and Auditing | Ensure rsyslog default file permissions configured | | | RHEL 7 - Logging and Auditing | Ensure rsyslog is configured to send logs to a remote log host | | | RHEL 7 - Logging and Auditing | Ensure syslog-ng default file permissions configured | | | RHEL 7 - Logging and Auditing | Ensure auditing for processes that start prior to auditd is enabled | | | RHEL 7 - Logging and Auditing | Ensure events that modify date and time information are collected | | | RHEL 7 - Logging and Auditing | Ensure events that modify user/group information are collected | | | RHEL 7 - Logging and Auditing | Ensure events that modify the system's network environment are collected | | | RHEL 7 - Logging and Auditing | Ensure events that modify the system's Mandatory Access Controls are collected | | | RHEL 7 - Logging and Auditing | Ensure login and logout events are collected | | | RHEL 7 - Logging and Auditing | Ensure session initiation information is collected | | | RHEL 7 - Logging and Auditing | Ensure discretionary access control permission modification events are collected | | | RHEL 7 - Logging and Auditing | Ensure unsuccessful unauthorized file access attempts are collected | | | RHEL 7 - Logging and Auditing | Ensure successful file system mounts are collected | | | RHEL 7 - Logging and Auditing | Ensure file deletion events by users are collected | | | RHEL 7 - Logging and Auditing | Ensure system administrator actions (sudolog) are collected | | | RHEL 7 - Logging and Auditing | Ensure the audit configuration is immutable | | | RHEL 7 - Logging and Auditing | Ensure audit log storage size is configured | | | RHEL 7 - Logging and Auditing | Ensure system is disabled when audit logs are full | | | RHEL 7 - Logging and Auditing | Ensure audit logs are not automatically deleted | | | RHEL 7 - Network Configuration | Ensure IP forwarding is disabled | | | RHEL 7 - Network Configuration | Ensure packet redirect sending is disabled | | | RHEL 7 - Network Configuration | Ensure source routed packets are not accepted | | | RHEL 7 - Network Configuration | Ensure ICMP redirects are not accepted | | | RHEL 7 - Network Configuration | Ensure secure ICMP redirects are not accepted | | | RHEL 7 - Network Configuration | Ensure suspicious packets are logged | | | RHEL 7 - Network Configuration | Ensure broadcast ICMP requests are ignored | | | RHEL 7 - Network Configuration | Ensure bogus ICMP responses are ignored | | | RHEL 7 - Network Configuration | Ensure Reverse Path Filtering is enabled | | | RHEL 7 - Services | Ensure X Window System is not installed | | | RHEL 7 - Services | Ensure time synchronization is in use | | | RHEL 7 - Services | Ensure ntp is configured | | | RHEL 7 - Services | Ensure chrony is configured | | | RHEL 7 - Services | Ensure NIS Client is not installed | | | RHEL 7 - Services | Ensure rsh client is not installed | | | RHEL 7 - Services | Ensure talk client is not installed | | | RHEL 7 - Services | Ensure telnet client is not installed | | | RHEL 7 - Services | Ensure LDAP client is not installed | | |Added following 3 Azure Data Lake policies
| **Category** | **Policy Title** | |-------------------------------|--------------------------------------------------------------------------------------| | Azure - Storage and Databases | Ensure that firewall is enabled for Azure Data Lake Storage Gen1 | | Azure - Storage and Databases | Ensure that encryption of sensitive data is enabled for Azure Data Lake Storage Gen1 | | Azure - Storage and Databases | Ensure that diagnostics log is enabled for Azure Data Lake Storage Gen1 |M365 IAM policies added
| **Category** | **Policy Title** | |------------------------------|----------------------------------------------------------------------------------------------------------------------| | Identity | Ensure that 'Number of methods required to reset' is set to '2' | | Identity | Ensure that 'Number of days before users are asked to re-confirm their authentication information' is not set to '0' | | Identity | Ensure that 'Notify users on password resets?' is set to 'Yes | | Identity | Ensure that 'Notify all admins when other admins reset their password?' is set to 'Yes' | | Identity | Ensure that 'Users can consent to apps accessing company data on their behalf' is set to 'No' | | Identity | Ensure that 'Users can add gallery apps to their Access Panel' is set to 'No' | | Identity | Ensure that 'Users can register applications' is set to 'No' | | Identity | Ensure that 'Guest user permissions are limited' is set to 'Yes' | | Identity | Ensure that 'Members can invite' is set to 'No' | | Identity | Ensure that 'Guests can invite' is set to 'No' | | Identity | Ensure that 'Restrict access to Azure AD administration portal' is set to 'Yes' | | Identity | Ensure that 'Self-service group management enabled' is set to 'No' | | Identity | Ensure that 'Users can create security groups' is set to 'No' | | Identity | Ensure that 'Users who can manage security groups' is set to 'None' | | Identity | Ensure that 'Users can create Office 365 groups' is set to 'No' | | Identity | Ensure that 'Users who can manage Office 365 groups' is set to 'None' | | Identity | Ensure that 'Enable All Users group' is set to 'Yes' | | Identity | Ensure that 'Require Multi-Factor Auth to join devices' is set to 'Yes' | - Updated following 115 Azure security center policies to support Azure Management Group level scope and show No Data as default behaviour. References [Configure ASC policies at Management Group level](../../remediation/azureQuickWins/#configure-azure-security-center-policies-azure-security-center)ASC Policy list updated
| **Policy Title** | **Category** | |-----------------------------------------------------------------------------------------------------------------------|-------------------------| | Azure - Security Center | Ensure that AAD authentication in Service Fabric is set to enabled in ASC | Azure - Security Center | | Azure - Security Center | Ensure that required diagnostic logs retention period in days for Batch accounts is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Azure Search service is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Data Lake Analytics is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Data Lake Store accounts is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Event Hub accounts is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in IoT Hub accounts is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Key Vault vaults is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Logic Apps workflows is set in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Service Bus is set in ASC | | Azure - Security Center | Ensure that monitoring of Kubernetes Services without RBAC is enabled in ASC | | Azure - Security Center | Ensure that monitoring of sensitive data is classified on SQL database is enabled in ASC | | Azure - Security Center | Ensure that monitoring of SQL managed instances alerts being sent to admins and subscription owners is enabled in ASC | | Azure - Security Center | Ensure that monitoring of classic storage accounts migration to ARM is enabled in ASC | | Azure - Security Center | Ensure that reporting of system updates in virtual machine scale sets is enabled in ASC | | Azure - Security Center | Ensure that monitoring of unencrypted SQL databases is enabled in ASC | | Azure - Security Center | Ensure that monitoring of classic virtual machines is enabled in ASC | | Azure - Security Center | Ensure that OS vulnerabilities monitoring for virtual machine scale sets is enabled in ASC | | Azure - Security Center | Ensure that the detection of VM vulnerabilities by a Vulnerability Assessment solution is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Redis Cache is set to enabled in ASC | | Azure - Security Center | Ensure that Vulnerability Assessment on your SQL servers is enabled in ASC | | Azure - Security Center | Ensure that monitoring of the use of HTTPS in Web App is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Search Service is set to enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Service Bus is set to enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Virtual Machine Scale Sets is set to enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Stream Analytics is set to enabled in ASC | | Azure - Security Center | Ensure that disable unrestricted network to storage account is set to enabled in ASC | | Azure - Security Center | Ensure that monitor disk encryption is set to enabled in ASC | | Azure - Security Center | Ensure that monitor for Endpoint Protection is set to enabled in ASC | | Azure - Security Center | Ensure that AAD authentication in SQL server is set to enabled in ASC | | Azure - Security Center | Ensure that MFA is enabled for all subscription accounts with owner permissions in ASC | | Azure - Security Center | Ensure that MFA is enabled for all subscription accounts with read permissions in ASC | | Azure - Security Center | Ensure that MFA is enabled for all subscription accounts with write permissions in ASC | | Azure - Security Center | Ensure that deprecated accounts is removed on subscription are set to enabled in ASC | | Azure - Security Center | Ensure that deprecated accounts with owner permissions are removed from subscription is set to enabled in ASC | | Azure - Security Center | Ensure that external accounts with owner permissions are removed from subscription is set to enabled in ASC | | Azure - Security Center | Ensure that external accounts with read permissions are removed from subscription is set to enabled in ASC | | Azure - Security Center | Ensure that external accounts with write permissions are removed from subscription is set to enabled in ASC | | Azure - Security Center | Ensure that monitor of Adaptive Application whitelisting is set to enabled in ASC | | Azure - Security Center | Ensure that metric alerts in Batch account is set to enabled in ASC | | Azure - Security Center | Ensure that namespace authorization rules in service bus is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of network security groups is set to enabled in ASC | | Azure - Security Center | Ensure that next generation firewall is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of OS vulnerabilities is set to enabled in ASC | |Azure - Security Center | Ensure that secure transfer to storage account is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of SQL auditing is set to enabled in ASC | | Azure - Security Center | Ensure that SqlDb Vulnerability Assesment is set to enabled in ASC | | Azure - Security Center | Ensure that monitor SQL encryption is set to enabled in ASC | | Azure - Security Center | Ensure that monitor storage blob encryption is set to enabled in ASC | | Azure - Security Center | Ensure that monitor system updates is set to enabled in ASC | | Azure - Security Center | Ensure that vulnerability assessment is set to enabled in ASC | | Azure - Security Center | Ensure that web application firewall is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of permissive network access to app-services is enabled in ASC | |Azure - Security Center | Ensure that Cluster Protection level in Service Fabric is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of SQL managed server without Advanced Data Security is enabled in ASC | | Azure - Security Center | Ensure that all Advanced Threat Protection types on SQL server is enabled in ASC | | Azure - Security Center | Ensure that monitoring of access rules in Event Hub namespaces is enabled in ASC | | Azure - Security Center | Ensure that monitoring of the use of HTTPS in API app is enable in ASC | | Azure - Security Center | Ensure that the Audit monitoring of SQL Servers is enabled in ASC | | Azure - Security Center | Ensure that monitoring of using built-in RBAC rules is enabled in ASC | | Azure - Security Center | Ensure that monitoring of access rules in Event Hubs is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Kubernetes Services without authorized IP ranges is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Automation Account Encryption is enabled in ASC | | Azure - Security Center | Ensure that monitoring of CORS restrictions for API Function is enabled in ASC | | Azure - Security Center | Ensure that monitoring of CORS restrictions for API Web is enabled in ASC | |Azure - Security Center | Ensure that monitoring of DDoS protection for virtual network is enabled in ASC | | Azure - Security Center | Ensure that monitoring of diagnostics logs in selective app services is enabled in ASC | | Azure - Security Center | Ensure that monitoring of diagnostic logs in IoT Hubs is enabled in ASC | | Azure - Security Center | Ensure that endpoint protection monitoring for virtual machine scale sets is enabled in ASC | | Azure - Security Center | Ensure that 'Send alerts to' is set in SQL server Advanced Data Security settings is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Data Lake Analytics is set to enabled in ASC | | Azure - Security Center | Ensure that IP Forwarding monitoring on virtual machines is disabled in ASC | | Azure - Security Center | Ensure that monitoring of network just In time access is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Open Management Ports on virtual machines is enabled in ASC | | Azure - Security Center | Ensure that monitoring of IP restrictions for API App is enabled in ASC | |Azure - Security Center | Ensure that monitoring of IP restrictions for Function App is enabled in ASC | |Azure - Security Center | Ensure that monitoring of IP restrictions for Web App is enabled in ASC | |Azure - Security Center | Ensure that monitoring of diagnostics logs in App Services is enabled in ASC | | Azure - Security Center | Ensure that monitoring of web sockets for API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of web sockets for Function App is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Data Lake Store is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of Endpoint Protection is enabled in ASC | | Azure - Security Center | Ensure that monitoring of custom domain use in API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of custom domain use in Function App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of custom domain use in Web App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of .Net version in API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of .Net version in Web App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Java version in API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Java version in web app is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Node.js version in Web App is enabled in ASC | |Azure - Security Center | Ensure that diagnostics logs in Event Hub is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of PHP version in Web App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Python version in API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Python version in Web App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Internet-facing VM for NSG traffic hardening is enabled in ASC | | Azure - Security Center | Ensure that monitoring of NSG for virtual machines is enabled in ASC | | Azure - Security Center | Ensure that monitoring of NSG for Subnet is enabled in ASC | | Azure - Security Center | Ensure that monitoring of Kubernetes Services without pod security policy is enabled in ASC | | Azure - Security Center | Ensure that monitoring of remote debugging for API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of remote debugging for Function App is enabled in ASC | |Azure - Security Center | Ensure that diagnostics logs in Key Vault is set to enabled in ASC | |Azure - Security Center | Ensure that monitoring of remote debugging for Web App is enabled in ASC | | Azure - Security Center | Ensure that required diagnostic logs retention period in days in Stream Analytics is set in ASC | |Azure - Security Center | Ensure that Vulnerability Assessment on your SQL managed instances is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Logic Apps is set to enabled in ASC | | Azure - Security Center | Ensure that JIT network access policy is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of SQL managed instances without Advanced Data Security is enabled in ASC | | Azure - Security Center | Ensure that all Advanced Threat Protection types on SQL managed instance is enabled in ASC | | Azure - Security Center | Ensure that monitoring of auditing policy Action-Groups and Actions setting is enabled in ASC | | Azure - Security Center | Ensure that diagnostics logs in Batch Account is set to enabled in ASC | | Azure - Security Center | Ensure that monitoring of CORS restrictions for API App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of the use of HTTPS in function app is enabled in ASC | | Azure - Security Center | Ensure that monitoring of web sockets for Web App is enabled in ASC | | Azure - Security Center | Ensure that monitoring of PHP version in the API App is enabled in ASC |
**February 2020 - v2.25.1**
----------------------------
1. **User Experience Improvements**
- **Private Benchmarks** : Added audit log, reports, and email notifications for an association to an active License.
2. **Platform & Stability Improvements**
* Fixed following bugs
- Extra categories are visible in the Baseline benchmark list
- Incorrect x/y count found for policy -> Ensure that 'Send alerts to' in Advanced Threat Protection Settings is set for SQL database
- 'Ensure Log Exports feature is enabled for Oracle instances' policy audit/remediation procedure is incorrect
- 'Ensure Log Exports feature is enabled for RDS MySQL Instance': Audit log is invalid for latest versions of mySQL instances
3. **Policies & Benchmarks Additions/Updates**
* Added the following 5 new security policies for Office 365 cloud account. To get data for these policies, please provide version 1.3 while executing the script for upgrade or creation of Office 365 advance security configuration.
- References
- [Upgrading the existing Office 365 account](../../onboardingGuide/office365AdvanceSecurityConfigurationUpgrade/)
- [Onboarding new Office 365 account](../../onboardingGuide/office365Subscription/) and [Creation of Advanced security configurations.](../../onboardingGuide/office365Subscription/#step-3-advanced-security-configurations/)
**January 2020 - v2.24.1**
----------------------------
1. **User Experience Improvements**
- Added email notifications to collaborators of private benchmark
2. **Platform & Stability Improvements**
* Fixed following bugs
- Private benchmark: Associated/Dissociated benchmarks are not visible under Private Benchmark tab unless user refreshes the UI
- Private benchmark: Private benchmark details are not opening in single click on navigating to the benchmark list page
- Private benchmark: Incorrect total count of policies in a category on Configure Benchmark
- Private benchmark: Arrow button is inconsistent for Private Benchmark 'configurations'
- Manage Users: Email notification not received on adding Account user
- Duplicate policies found for SQL Server for NIST-CSF benchmark
3. **Policies & Benchmarks Additions/Updates**
**January 2020 - v2.23.1**
----------------------------
1. **Features & User Experience Improvements**
- **Private Benchmark** : Cloudneeti offers an ability for Organizations to create their own Information Security benchmark by either deriving from an existing baseline of Cloudneeti supported benchmarks or by creating completely on your own. Refer documentation for more details here.
- **Audit Report API:** Cloudneeti offers an Audit report API to get automated access of security and compliance posture. This API is part of a larger set of features for a deeper integration with DevOps and Risk Auditors tooling. Refer details here.
- Added consistent tooltip across Compliance, Security, Risk, Asset dashboards, and benchmark summary pages.
2. **Platform & Stability Improvements**
* Fixed following bugs
- Delete Account User email notification missing
- Fixed the implementation of Application Gateway policies for TLS version 1.0,1.1 and 1.2
3. **Policies & Benchmarks Additions/Updates**